cisco 350-501 Exam Questions
Questions for the 350-501 were updated on : Jul 08 ,2025
Page 1 out of 12. Viewing questions 1-15 out of 166
Question 1 Topic 1
Topic 1
DRAG DROP
Drag and drop the OSs from the left onto the correct descriptions on the right.
Select and Place: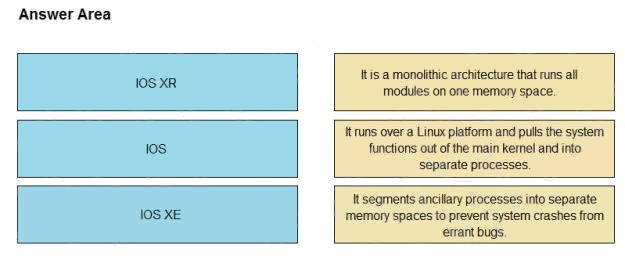
Answer:
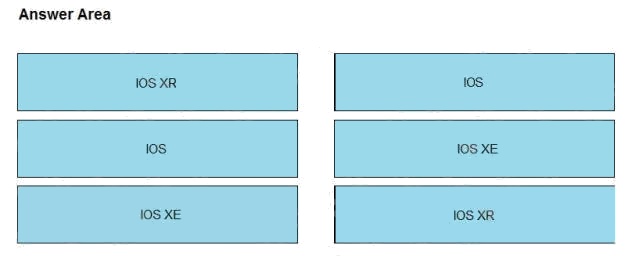
Explanation:
Reference: https://specialties.bayt.com/en/specialties/q/276369/what-is-the-key-difference-between-ios-ios-xe-and-ios-xr-for-
cisco-devices/
Question 2 Topic 1
Topic 1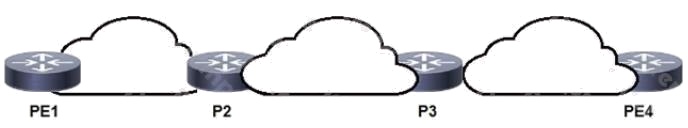
Refer to the exhibit. P3 and PE4 are at the edge of the service provider core and serve as ABR routers. Aggregation areas
are on either side of the core.
Which statement about the architecture is true?
- A. To support seamless MPLS, the BGP route reflector feature must be disabled.
- B. If each area is running its own IGP, BGP must provide an end-to-end MPLS LSP.
- C. If each area is running its own IGP, the ABR routers must redistribute the IGP routing table into BGP.
- D. To support seamless MPLS, TDP must be used as the label protocol.
Answer:
B
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9600/software/release/16-
12/configuration_guide/mpls/b_1612_mpls_9600_cg/configuring_seamless_mpls.html
Question 3 Topic 1
Topic 1
Which component is similar to an EVPN instance?
- A. router distinguisher
- B. MPLS label
- C. IGP router ID
- D. VRF
Answer:
D
Question 4 Topic 1
Topic 1
Why do Cisco MPLS TE tunnels require a link-state routing protocol?
- A. The link-state database provides segmentation by area, which improves the path-selection process.
- B. The link-state database provides a data repository from which the tunnel endpoints can dynamically select a source ID.
- C. Link-state routing protocols use SPF calculations that the tunnel endpoints leverage to implement the tunnel.
- D. The tunnel endpoints use the link-state database to evaluate the entire topology and determine the best path.
Answer:
D
Question 5 Topic 1
Topic 1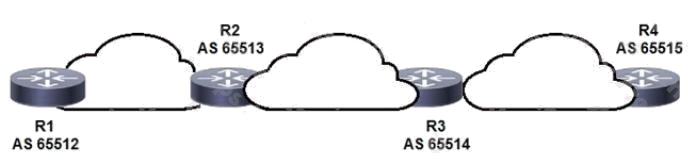
Refer to the exhibit. BGPsec is implemented on R1, R2, R3, and R4. BGP peering is established between neighboring
autonomous systems.
Which statement about implementation is true?
- A. BGP updates from the iBGP peers are appended with a community of local-as.
- B. BGP updates from the all BGP peers are appended with a community of no-export.
- C. BGP updates from the eBGP peers are appended with an additional AS path value that is statically set by the domain administrator.
- D. BGP updates from the eBGP peers are appended with a BGPsec attribute sequence that includes a public key hash and digital signature.
Answer:
D
Question 6 Topic 1
Topic 1
You are configuring MPLS traffic-engineering tunnels in the core. Which two ways exist for the tunnel path across the core?
(Choose two.)
- A. The dynamic path option is supported only with IS-IS.
- B. Tunnels can be configured with dynamic path or explicitly defined path.
- C. A zero bandwidth tunnel is not a valid option.
- D. The bandwidth statement creates a “hard” reservation on the link.
- E. Tunnel links inherit IGP metrics by default unless overridden.
Answer:
B E
Question 7 Topic 1
Topic 1
Which configuration mode do you use to apply the mpls ldp graceful-restart command in IOS XE Software?
- A. MPLS LDP neighbor
- B. interface
- C. MPLS
- D. global
Answer:
D
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/mp_ha/configuration/xe-3s/mp-ha-xe-3s-book/mp-ldp-grace-
rstrt.html
Question 8 Topic 1
Topic 1
After you analyze your network environment, you decide to implement a full separation model for Internet access and MPLS
L3VPN services.
For which reason do you make this decision?
- A. It enables EGP and IGP to operate independently.
- B. It enables you to choose whether to separate or centralize each individual service.
- C. It is easier to manage a system in which services are mixed.
- D. It requires only one edge router.
Answer:
A
Question 9 Topic 1
Topic 1
Which statement about the Cisco MPLS TE forwarding adjacency feature is true?
- A. It enables the MPLS core to use EIGRP as the routing protocol.
- B. It enables the Cisco MPLS TE tunnel to be advertised into the running IGP.
- C. It enables the tailend router to advertise routes to the headend router over the tunnel.
- D. It enables the headend and tailend routers to establish a bidirectional tunnel.
Answer:
B
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/mp_te_path_setup/configuration/xe-16/mp-te-path-setup-xe-
16-book/mpls-traffic-engineering-forwarding-adjacency.pdf
Question 10 Topic 1
Topic 1
While implementing TTL security, you issue the PE(config-router-af)#neighbor 2.2.2.2 ttl-security hops 2 command.
After you issue this command, which BGP packets does the PE accept?
- A. to 2.2.2.2, with a TTL of 2 or more
- B. from 2.2.2.2, with a TTL of less than 2
- C. to 2.2.2.2, with a TTL of less than 253
- D. from 2.2.2.2, with a TTL of 253 or more
Answer:
D
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/ios/12_2sx/feature/guide/fsxebtsh.html#wp1059215
Question 11 Topic 1
Topic 1
Refer to the exhibits. Which information is provided for traceback analysis when this configuration is applied?
- A. source interface
- B. packet size distribution
- C. IP sub flow cache
- D. BGP version
Answer:
C
Question 12 Topic 1
Topic 1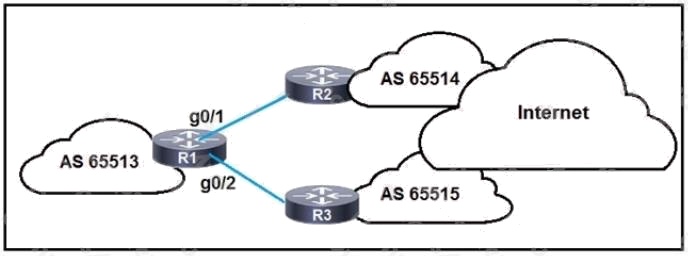
Refer to the exhibit. R1 is connected to two service providers and is under a DDoS attack.
Which statement about this design is true if URPF in strict mode is configured on both interfaces?
- A. R1 drops all traffic that ingresses either interface that has a FIB entry that exits a different interface.
- B. R1 drops destination addresses that are routed to a null interface on the router.
- C. R1 permits asymmetric routing as long as the AS-PATH attribute entry matches the connected AS.
- D. R1 accepts source addresses on interface gigabitethernet0/1 that are private addresses.
Answer:
A
Question 13 Topic 1
Topic 1
Refer to the exhibit. Router 1 was experiencing a DDoS attack that was traced to interface gigabitethernet0/1.
Which statement about this configuration is true?
- A. Router 1 accepts all traffic that ingresses and egresses interface gigabitethernet0/1.
- B. Router 1 drops all traffic that ingresses interface gigabitethernet0/1 that has a FIB entry that exits a different interface.
- C. Router 1 accepts source addresses that have a match in the FIB that indicates it is reachable through a real interface.
- D. Router 1 accepts source addresses on interface gigabitethernet0/1 that are private addresses.
Answer:
C
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/switches/datacenter/sw/4_1/nx-os/security/configuration/guide/sec_nx-os-
cfg/sec_urpf.html
Question 14 Topic 1
Topic 1
Refer to the exhibit. An engineer is preparing to implement data plane security configuration.
Which statement about this configuration is true?
- A. Router 2 is the router receiving the DDoS attack.
- B. Router 1 must be configured with uRPF for the RTBH implementation to be effective.
- C. Router 1 is the trigger router in a RTBH implementation.
- D. Router 2 must configure a route to null 0 for network 192.168.1.0/24 for the RTBH implementation to be complete.
Answer:
A
Question 15 Topic 1
Topic 1
Which configuration modifies Local Packet Transport Services hardware policies?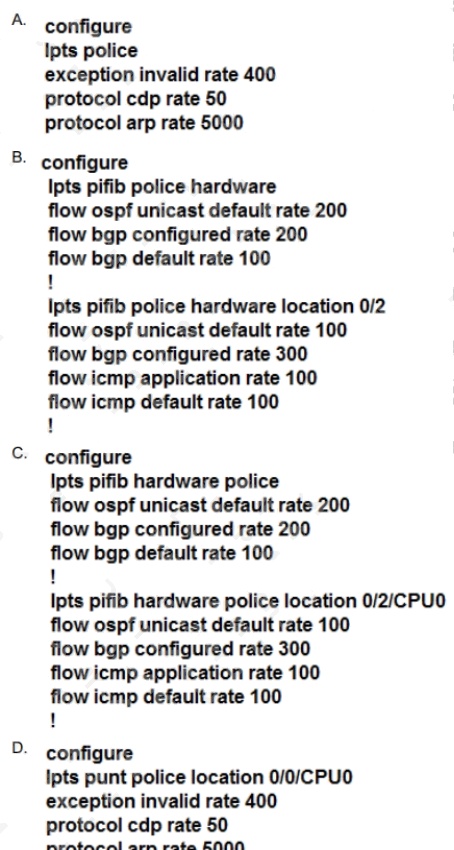

- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
C
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/routers/crs/software/crs_r4-
1/addr_serv/command/reference/b_ipaddr_cr41crs/b_ipaddr_cr41crs_chapter_0111.html#wp1754734006