cisco 350-201 Exam Questions
Questions for the 350-201 were updated on : Jul 08 ,2025
Page 1 out of 10. Viewing questions 1-15 out of 139
Question 1
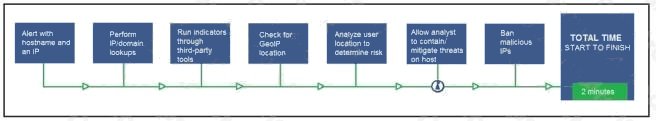
Refer to the exhibit. An engineer configured this SOAR solution workflow to identify account theft threats and privilege
escalation, evaluate risk, and respond by resolving the threat. This solution is handling more threats than Security analysts
have time to analyze. Without this analysis, the team cannot be proactive and anticipate attacks. Which action will
accomplish this goal?
- A. Exclude the step “BAN malicious IP” to allow analysts to conduct and track the remediation
- B. Include a step “Take a Snapshot” to capture the endpoint state to contain the threat for analysis
- C. Exclude the step Check for GeoIP location to allow analysts to analyze the location and the associated risk based on asset criticality
- D. Include a step “Reporting” to alert the security department of threats identified by the SOAR reporting engine
Answer:
A
Question 2
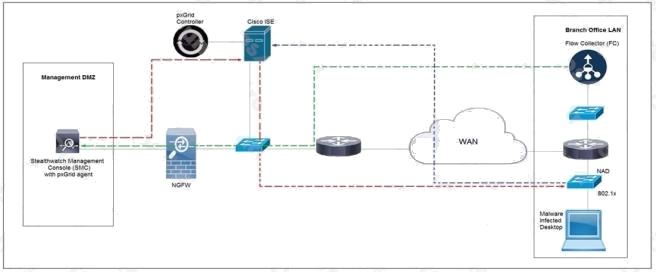
Refer to the exhibit. Rapid Threat Containment using Cisco Secure Network Analytics (Stealthwatch) and ISE detects the
threat of malware-infected 802.1x authenticated endpoints and places that endpoint into a quarantine VLAN using Adaptive
Network Control policy. Which method was used to signal ISE to quarantine the endpoints?
- A. SNMP
- B. syslog
- C. REST API
- D. pxGrid
Answer:
C
Question 3
Refer to the exhibit. For IP 192.168.1.209, what are the risk level, activity, and next step?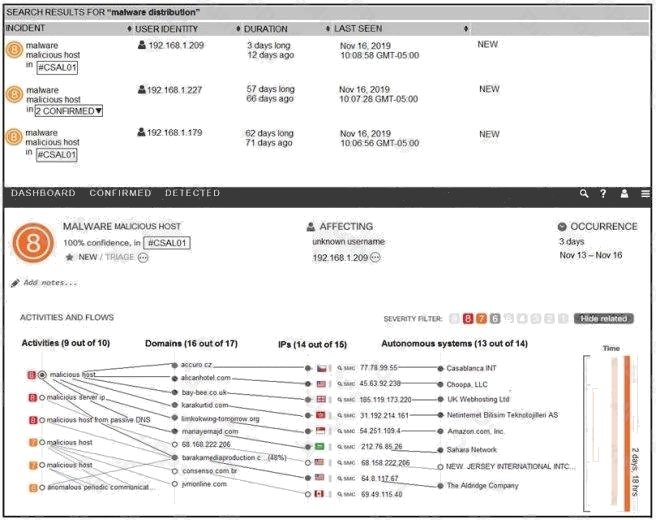
- A. high risk level, anomalous periodic communication, quarantine with antivirus
- B. critical risk level, malicious server IP, run in a sandboxed environment
- C. critical risk level, data exfiltration, isolate the device
- D. high risk level, malicious host, investigate further
Answer:
A
Question 4
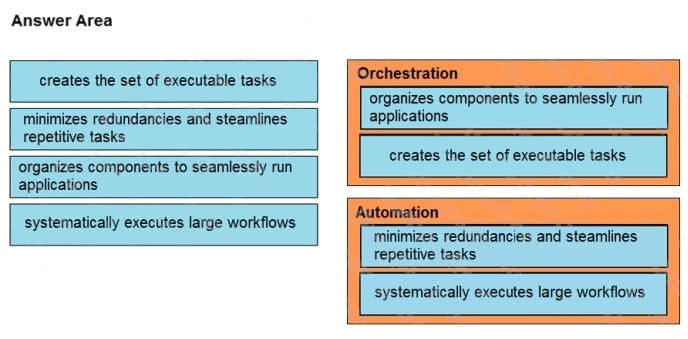
DRAG DROP
Drag and drop the function on the left onto the mechanism on the right.
Select and Place: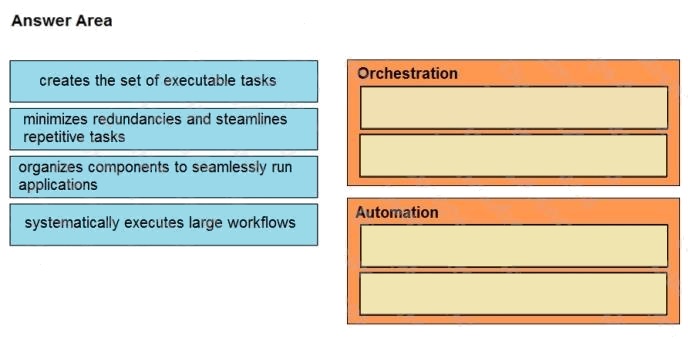
Answer:
Question 5
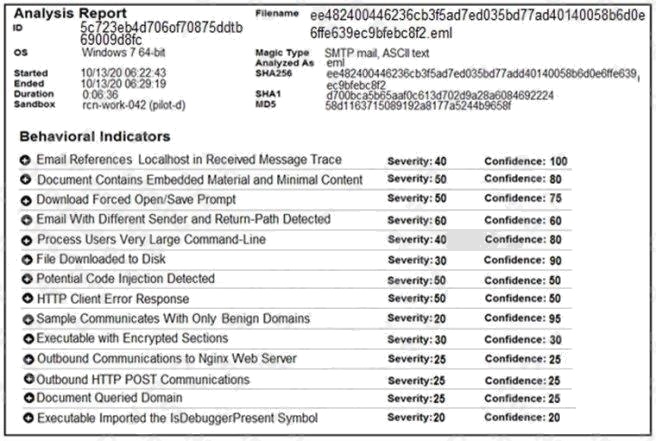
Refer to the exhibit. Cisco Advanced Malware Protection installed on an end-user desktop automatically submitted a low
prevalence file to the Threat Grid analysis engine. What should be concluded from this report?
- A. Threat scores are high, malicious ransomware has been detected, and files have been modified
- B. Threat scores are low, malicious ransomware has been detected, and files have been modified
- C. Threat scores are high, malicious activity is detected, but files have not been modified
- D. Threat scores are low and no malicious file activity is detected
Answer:
B
Question 6
An engineer is investigating several cases of increased incoming spam emails and suspicious emails from the HR and
service departments. While checking the event sources, the website monitoring tool showed several web scraping alerts
overnight. Which type of compromise is indicated?
- A. phishing
- B. dumpster diving
- C. social engineering
- D. privilege escalation
Answer:
C
Question 7
Refer to the exhibit. Which command was executed in PowerShell to generate this log?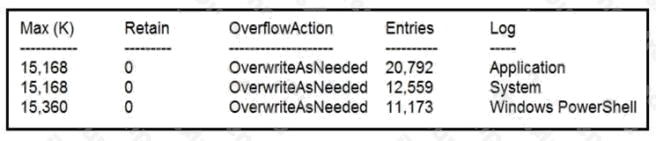
- A. Get-EventLog -LogName*
- B. Get-EventLog -List
- C. Get-WinEvent -ListLog* -ComputerName localhost
- D. Get-WinEvent -ListLog*
Answer:
A
Explanation:
Reference: https://lists.xymon.com/archive/2019-March/046125.html
Question 8
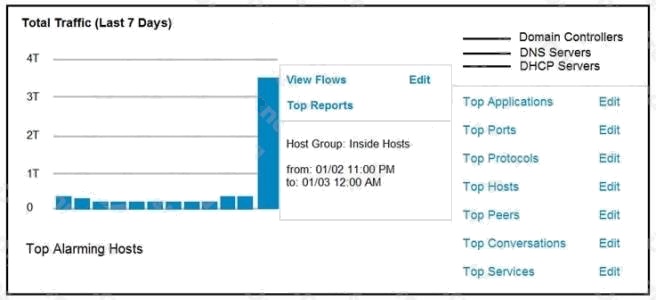
Refer to the exhibit. An engineer notices a significant anomaly in the traffic in one of the host groups in Cisco Secure
Network Analytics (Stealthwatch) and must analyze the top data transmissions. Which tool accomplishes this task?
- A. Top Peers
- B. Top Hosts
- C. Top Conversations
- D. Top Ports
Answer:
B
Explanation:
Reference: https://www.ciscolive.com/c/dam/r/ciscolive/emea/docs/2018/pdf/BRKSEC-3014.pdf
Question 9
An audit is assessing a small business that is selling automotive parts and diagnostic services. Due to increased customer
demands, the company recently started to accept credit card payments and acquired a POS terminal. Which compliance
regulations must the audit apply to the company?
- A. HIPAA
- B. FISMA
- C. COBIT
- D. PCI DSS
Answer:
D
Explanation:
Reference: https://upserve.com/restaurant-insider/restaurant-pos-pci-compliance-checklist/
Question 10
Where do threat intelligence tools search for data to identify potential malicious IP addresses, domain names, and URLs?
- A. customer data
- B. internal database
- C. internal cloud
- D. Internet
Answer:
D
Question 11
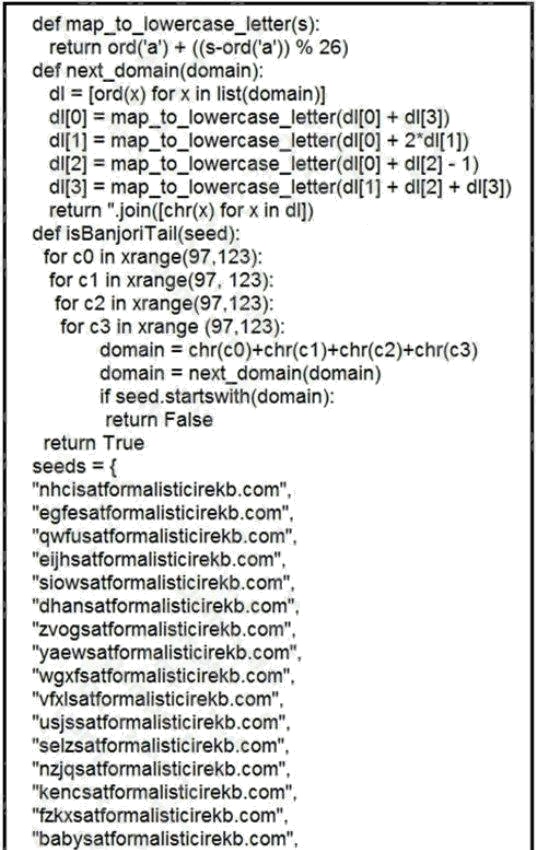
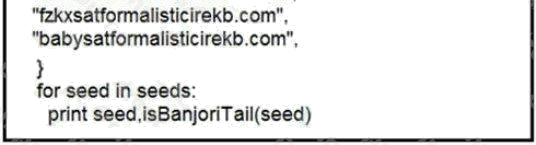
Refer to the exhibit. What results from this script?
- A. Seeds for existing domains are checked
- B. A search is conducted for additional seeds
- C. Domains are compared to seed rules
- D. A list of domains as seeds is blocked
Answer:
B
Question 12
A cloud engineer needs a solution to deploy applications on a cloud without being able to manage and control the server OS.
Which type of cloud environment should be used?
- A. IaaS
- B. PaaS
- C. DaaS
- D. SaaS
Answer:
A
Question 13
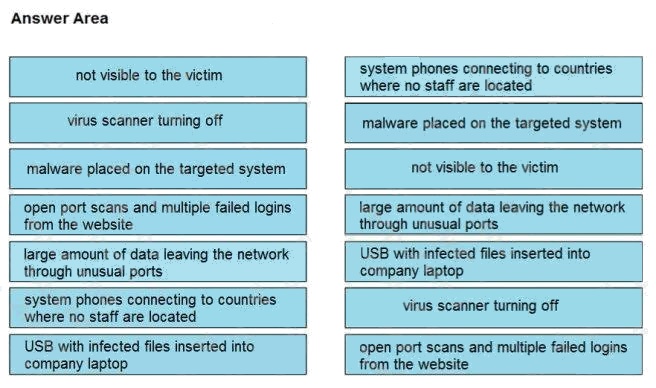
DRAG DROP
Drag and drop the type of attacks from the left onto the cyber kill chain stages at which the attacks are seen on the right.
Select and Place: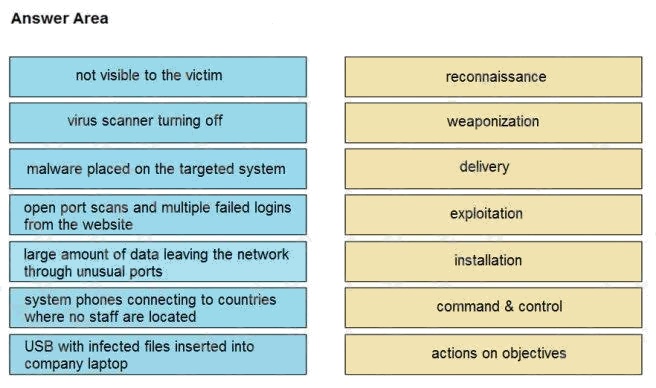
Answer:
Question 14
A new malware variant is discovered hidden in pirated software that is distributed on the Internet. Executives have asked for
an organizational risk assessment. The security officer is given a list of all assets. According to NIST, which two elements
are missing to calculate the risk assessment? (Choose two.)
- A. incident response playbooks
- B. asset vulnerability assessment
- C. report of staff members with asset relations
- D. key assets and executives
- E. malware analysis report
Answer:
B E
Explanation:
Reference: https://cloudogre.com/risk-assessment/
Question 15
A security expert is investigating a breach that resulted in a $32 million loss from customer accounts. Hackers were able to
steal API keys and two-factor codes due to a vulnerability that was introduced in a new code a few weeks before the attack.
Which step was missed that would have prevented this breach?
- A. use of the Nmap tool to identify the vulnerability when the new code was deployed
- B. implementation of a firewall and intrusion detection system
- C. implementation of an endpoint protection system
- D. use of SecDevOps to detect the vulnerability during development
Answer:
D
Explanation:
Reference: https://securityintelligence.com/how-to-prioritize-security-vulnerabilities-in-secdevops/