cisco 300-915 Exam Questions
Questions for the 300-915 were updated on : Jul 02 ,2025
Page 1 out of 5. Viewing questions 1-15 out of 61
Question 1
DRAG DROP
An application needs to calculate if the product meets a determined quality specification, activate an automation to remove
poor quality products, and report detailed results back to the cloud. All data are captured from an application that is
connected to a sensor. Using the SDK of the cloud provider, drag and drop the tasks that must be completed from the left to
the right. Not all options are used.
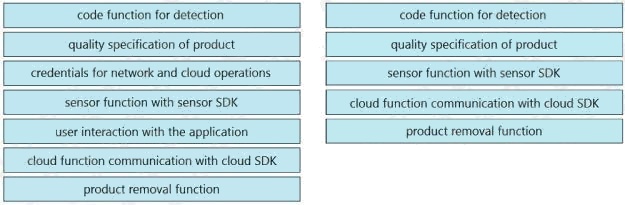
Select and Place: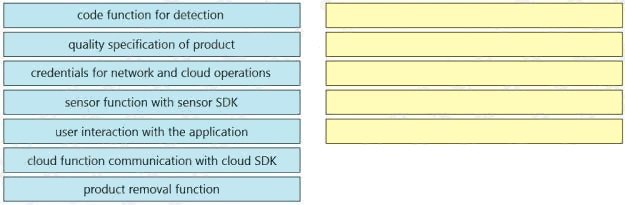
Answer:
Question 2
When constructing a Python script for data extraction using GMM APIs on a Cisco Kinetic Cloud platform, how should the
API authentication be implemented?
- A. Generate the API keys once and edit the permissions as needed.
- B. Generate and use the API keys for the required access level from the Kinetic Cloud application.
- C. Use a complex username and password with 128-bit encryption.
- D. Use a complex username with an auto-generated password from the Kinetic Cloud application.
Answer:
B
Question 3
After an application is deployed, potential issues arise around connectivity. As part of the troubleshooting process, the IP
address must be determined to ensure end-to-end communication.
Which method provides the required details using the Cisco IOx CLI?
- A. ioxclient application status
- B. ioxclient application metrics
- C. ioxclient application getconfig
- D. ioxclient application info
Answer:
D
Question 4
Where are edge data services typically instantiated?
- A. at the edge of network
- B. in the cloud
- C. in the data center
- D. in a private cloud
Answer:
A
Question 5
When trying to subscribe to an MQTT broker on the internet, the MQTT client is on a private subnet and must be NATed to
reach the public broker.
What is the expected outcome when this configuration is in place?
- A. The client periodically reconnects to the default gateway.
- B. The client connects only once using the PENDING message to the broker.
- C. The client periodically reconnects to the broker over the NAT connection.
- D. The client connects only once using the CONNECT massage to the broker.
Answer:
D
Question 6
Which two security approaches help build a strong authentication scheme? (Choose two.)
- A. connection based on location
- B. session IDs accepted only from cookies
- C. maximum allowed connections
- D. user logout
- E. session logout because of inactivity
Answer:
C E
Question 7
DRAG DROP
Drag and drop the Dockerfile instructions from the left onto the correct arguments on the right.
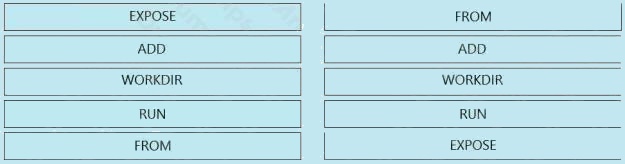
Select and Place: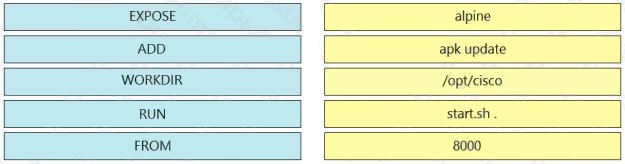
Answer:
Question 8
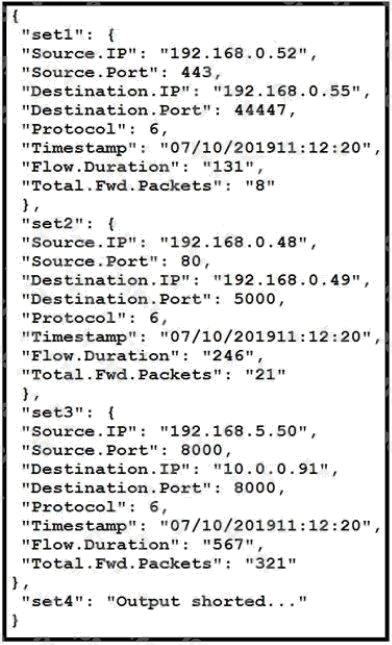
Refer to the exhibit. The code snippet provides information about the packet captures within a network.
How can the most used source IP addresses within a specific time be visualized?
- A. line graph
- B. bar histogram
- C. scatter plot
- D. heatmap
Answer:
B
Question 9
In a secure software development lifecycle process, what must be created as soon as the architecture is in place?
- A. integration plan
- B. test plan
- C. functional specification document
- D. threat modeling
Answer:
C
Question 10
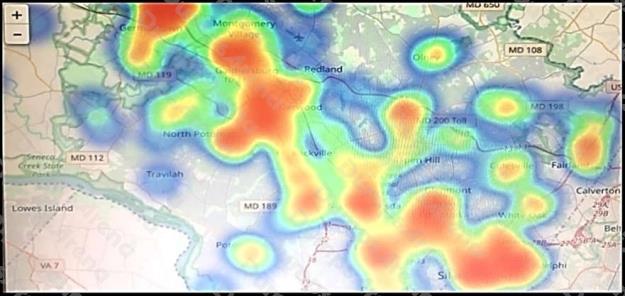
Refer to the exhibit. Which two statements are true? (Choose two.)
- A. That is a heatmap projected on top of a geographic map.
- B. That is a treemap projected on top of a geographic map.
- C. The color red usually stands for lower values and the color blue usually stands for higher values.
- D. Another suitable visualization technique for this image would be line graphs.
- E. The color blue usually stands for lower values and the color red usually stands for higher values.
Answer:
A E
Question 11
A company is collecting data from several thousand machines globally. Which software component in the overall architecture
is the next destination of the dataflow after the data has been gathered and normalized on the edge data software?
- A. relational database: MySQL
- B. historian database: influxDB
- C. message broker: Apache Kafka
- D. dashboard: Node.js web app
Answer:
B
Question 12
What are two functionalities of edge data services? (Choose two.)
- A. creating a machine learning data model
- B. supporting many interfaces and APIs
- C. applying advanced data analytics
- D. filtering, normalizing and aggregating data
- E. saving data for a prolonged time period
Answer:
D E
Question 13
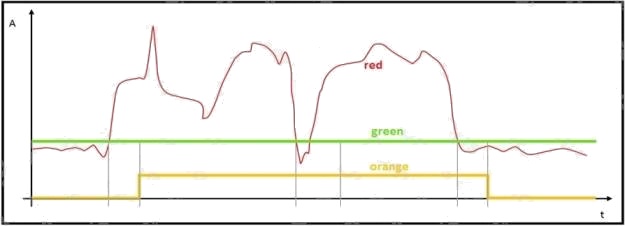
Refer to the exhibit. The red line represents the energy consumption of an industrial machine.
Which two statements about the graphs are true? (Choose two.)
- A. The orange graph is expected to drop to zero for a brief period around the midpoint on the x axis.
- B. The red graph contains the raw data points.
- C. The green graph is the mean value of the data points.
- D. The green graph does not give us any valuable information.
- E. The orange graph has three values on the y-axis.
Answer:
B C
Question 14
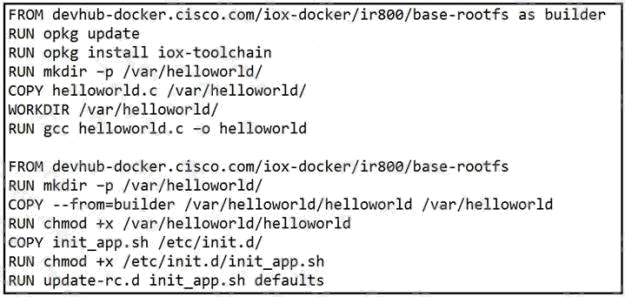
Refer to the exhibit. When a Docker image is built using this Dockerfile, which two statements are valid on Cisco IOx 1.8 and
before? (Choose two.)
- A. It builds an image that can be executed on all Cisco platforms.
- B. It builds a Docker image that cannot be used directly on Cisco IOx.
- C. It compiles a "hello world" program in C.
- D. It creates two separate images.
- E. It builds an IOx package that can be deployed directly.
Answer:
B C
Question 15
Which two commands inside a Docker container on a gateway help to troubleshoot why the compute performance of the
device is slowing down? (Choose two.)
- A. show processes
- B. top
- C. wmic
- D. ps
- E. proc
Answer:
B D