cisco 300-740 Exam Questions
Questions for the 300-740 were updated on : Jan 20 ,2026
Page 1 out of 5. Viewing questions 1-15 out of 61
Question 1
How does Cisco XDR perform threat prioritization by using its visibility across multiple platforms?
- A. By assigning priority based on the detection platform
- B. By correlating detection risk and asset value at risk
- C. By prioritizing threats based on their frequency across platforms
- D. By using a fixed priority system for all platforms
Answer:
B
Question 2
Refer to the exhibit.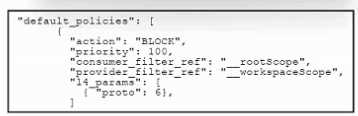
Refer to the exhibit. An engineer configured a default segmentation policy in Cisco Secure Workload
to block SMTP traffic. During testing, it is observed that the SMTP traffic is still allowed. Which action
must the engineer take to complete the configuration?
- A. Add "port": [25, 25] to _rootScope
- B. Add _SMTPScope to provider_filter_ref
- C. Add "port": [25, 25] to _params
- D. Change consumer_filter_ref to: _SMTPScope
Answer:
C
Question 3
A network administrator uses Cisco Umbrella to protect internal users from malicious content. A
customer is using an IPsec tunnel to connect to an Umbrella Organization. The administrator was
informed about a zero-day vulnerability that infects user machines and uploads sensitive data
through the RDP port. The administrator must ensure that no users are connected to the internet
using the RDP protocol. Which Umbrella configuration must the administrator apply?
- A. Web policy to block Remote Desktop Manager application type
- B. Firewall policy and set port 3389 to be blocked for all outgoing traffic
- C. Data loss prevention policy to block all file uploads with RDP application mime type
- D. DNS policy to block Remote Desktop Manager application type
Answer:
B
Question 4
Refer to the exhibit.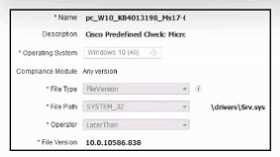
Refer to the exhibit. A security engineer must configure a posture policy in Cisco ISE to ensure that
employee laptops have a critical patch for WannaCry installed before they can access the network.
Which posture condition must the engineer configure?
- A. Patch Management Condition
- B. File Condition
- C. Anti-Virus Condition
- D. Anti-Malware Condition
Answer:
B
Question 5
Which web application firewall deployment in the Cisco Secure DDoS protects against application
layer and volumetric attacks?
- A. Hybrid
- B. On-demand
- C. Always-on
- D. Active/passive
Answer:
C
Question 6
DRAG DROP
Refer to the exhibit.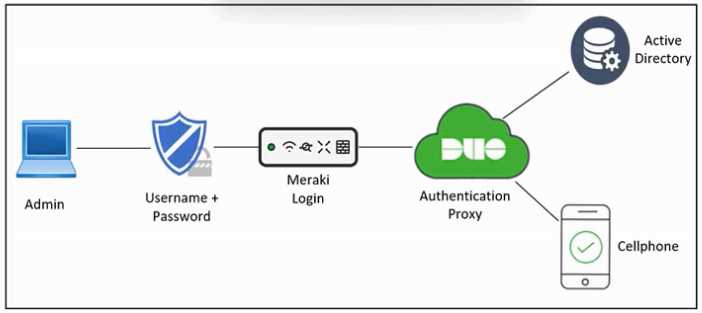
Refer to the exhibit. An engineer must configure multifactor authentication using the Duo Mobile
app to provide admin access to a Cisco Meraki switch. The engineer already configured Duo Mobile
and received an activation code. Drag and drop the steps from left to right to complete the
configuration.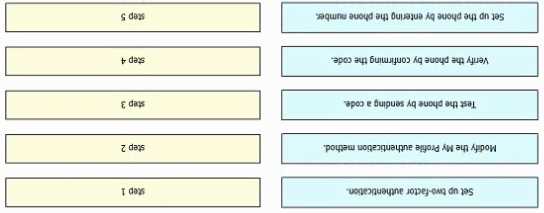
Answer:
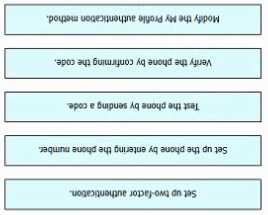
Question 7
According to the MITRE ATT&CK framework, which approach should be used to mitigate exploitation
risks?
- A. Performing regular data backups and testing recovery procedures
- B. Keeping systems updated with the latest patches
- C. Consistently maintaining up-to-date antivirus software
- D. Ensuring that network traffic is closely monitored and controlled
Answer:
B
Question 8
Refer to the exhibit.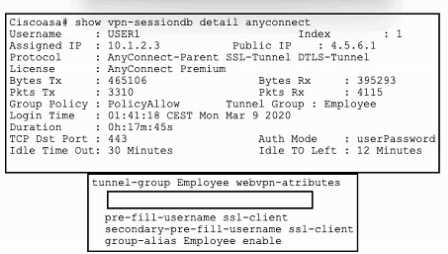
Refer to the exhibit. An engineer must implement a remote access VPN solution that provides user
and device verification. The company uses Active Directory for user authentication and ID certificates
for device identity. Users are currently able to connect using only a valid username and password,
even if their computer is missing the required certificate.
Which command from the Cisco ASA tunnel-group completes the requirement of verifying device
identity in addition to user identity?
- A. ldap-attribute-map PolicyAllow
- B. webvpn authorize-device
- C. authentication mfa
- D. authentication aaa certificate
Answer:
B
Question 9
Refer to the exhibit.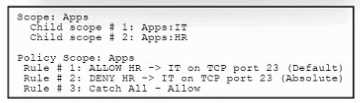
Refer to the exhibit. An engineer must analyze a segmentation policy in Cisco Secure Workload. What
is the result of applying the policy?
- A. The default catch-all rule is applied by using Rule #3.
- B. HR cannot use Telnet to connect to IT by using Rule #2.
- C. HR can use Telnet to connect to IT by using Rule #1.
- D. The explicit deny all rule is applied.
Answer:
B
Question 10
Refer to the exhibit.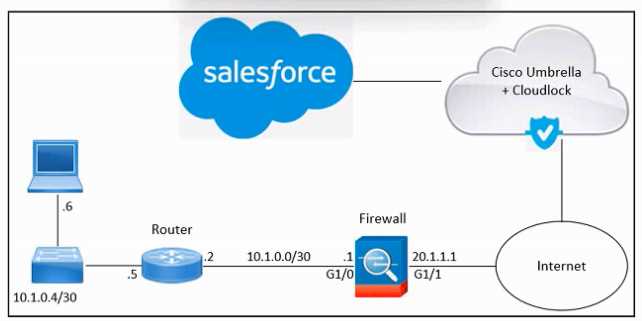
Refer to the exhibit. An engineer must enable access to Salesforce using Cisco Umbrella and Cisco
Cloudlock. These actions were performed:
From Salesforce, add the Cloudlock IP address to the allow list
From Cloudlock, authorize Salesforce
However, Salesforce access via Cloudlock is still unauthorized. What should be done to meet the
requirements?
- A. From the Salesforce admin page, grant API access to Cloudlock.
- B. From the Salesforce admin page, grant network access to Cloudlock
- C. From the Cloudlock dashboard, grant API access to Salesforce.
- D. From the Cloudlock dashboard, grant network access to Salesforce.
Answer:
A
Question 11
A recent InfraGard news release indicates the need to establish a risk ranking for all on-premises and
cloud services. The ACME Corporation already performs risk assessments for on-premises services
and has applied a risk ranking to them. However, the cloud services that were used lack risk rankings.
What Cisco Umbrella function should be used to meet the requirement?
- A. Secure Internet Gateway
- B. Domain Name Server Filtering
- C. URL Categorization by Talos
- D. App Discovery
Answer:
D
Question 12
Which SAFE component logically arranges the security capabilities into blueprints?
- A. Reference Architectures
- B. Cisco Validated Designs
- C. Places in the Network
- D. Secure Domains
Answer:
A
Question 13
Refer to the exhibit.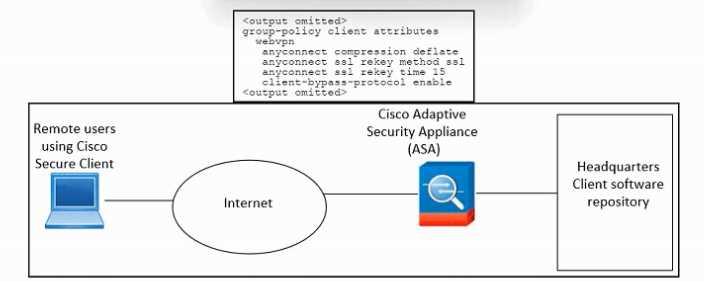
Refer to the exhibit. An engineer must configure Cisco ASA so that the Secure Client deployment is
removed when the user laptop disconnects from the VPN. The indicated configuration was applied to
the Cisco ASA firewall. Which command must be run to meet the requirement?
- A. client-bypass-protocol enable
- B. anyconnect keep-installer none
- C. anyconnect firewall-rule client-interface
- D. client-bypass-protocol disable
Answer:
D
Question 14
What does the Cisco Telemetry Broker provide for telemetry data?
- A. Data analytics
- B. Data mining
- C. Data filtering
- D. Data brokering
Answer:
D
Question 15
Refer to the exhibit.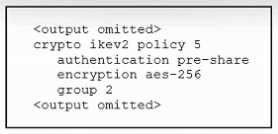
Refer to the exhibit. An engineer must configure a remote access IPsec/IKEv2 VPN that will use SHA-
512 on a Cisco ASA firewall. The indicated configuration was applied to the firewall; however, the
tunnel fails to establish. Which command must be run to meet the requirement?
- A. integrity sha512
- B. protocol esp encryption sha512
- C. ipsec-proposal sha512
- D. encryption sha512
Answer:
C