cisco 300-735 Exam Questions
Questions for the 300-735 were updated on : Feb 18 ,2026
Page 1 out of 4. Viewing questions 1-15 out of 60
Question 1
A developer has just completed the configuration of an API that connects sensitive internal systems.
Based on company policies, the security of the data is a high priority.
Which approach must be taken to secure API keys and passwords?
- A. Embed them directly in the code.
- B. Store them in a hidden file.
- C. Store them inside the source tree of the application.
- D. Change them periodically.
Answer:
D
Question 2
Which two methods are API security best practices? (Choose two.)
- A. Use tokens after the identity of a client has been established.
- B. Use the same operating system throughout the infrastructure.
- C. Use encryption and signatures to secure data.
- D. Use basic auth credentials over all internal API interactions.
- E. Use cloud hosting services to manage security configuration.
Answer:
AC
Question 3
DRAG DROP
Drag and drop the items to complete the curl request to the ThreatGRID API. The API call should
request the first 10 IP addresses that ThreatGRID saw samples communicate with during analysis, in
the first two hours of January 18th (UTC time), where those communications triggered a Behavior
Indicator that had a confidence equal to or higher than 75 and a severity equal to or higher than 95.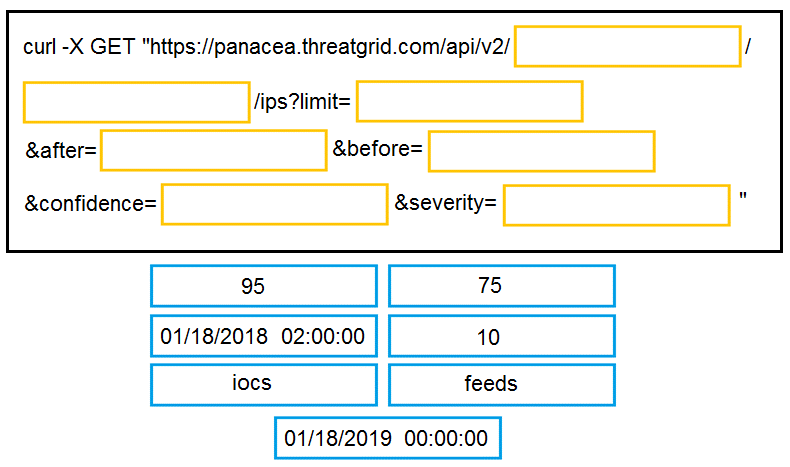
Answer:
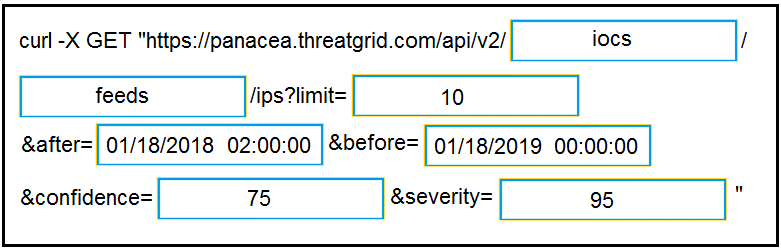
Reference:
https://support.umbrella.com/hc/en-us/articles/231248768-Cisco-Umbrella-Cisco-AMP-Threat-Grid-
Cloud
- Integration-Setup-Guide
Question 4
DRAG DROP
Drag and drop the code to complete the URL for the Cisco AMP for Endpoints API POST request so
that it will add a sha256 to a given file_list using file_list_guid.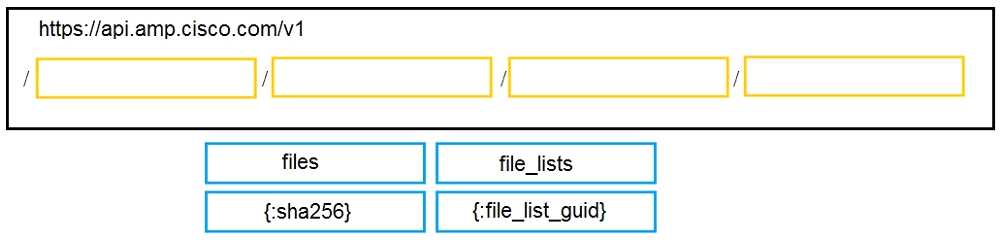
Answer:
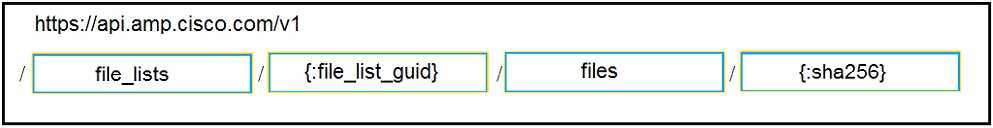
Reference:
https://api-docs.amp.cisco.com/api_actions/details?api_action=POST+%2Fv1%2Ffile_lists%2F%7B%
3Afile_list_guid%7D%2Ffiles%2F%7B%3Asha256%7D&api_host=api.eu.amp.cisco.com&api_resource
=File
+List+Item&api_version=v1
Question 5
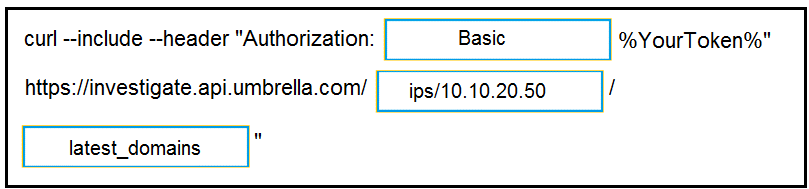
DRAG DROP
Drag and drop the code to complete the curl query to the Cisco Umbrella Investigate API for the
Latest Malicious Domains for the IP address 10.10.20.50. Not all options are used.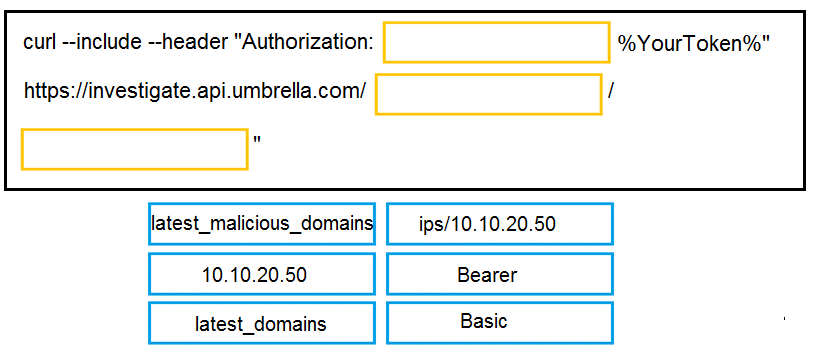
Answer:
Reference:
https://docs.umbrella.com/investigate-api/reference#about-the-api-and-authentication
Question 6
Which URI string is used to create a policy that takes precedence over other applicable policies that
are configured on Cisco Stealthwatch?
- A. /tenants/{tenantId}/policy/system/host-policy
- B. /tenants/{tenantId}/policy/system/role-policy
- C. /tenants/{tenantId}/policy/system
- D. /tenants/{tenantId}/policy/system/{policyId}
Answer:
A
Question 7
Which step is required by Cisco pxGrid providers to expose functionality to consumer applications
that are written in Python?
- A. Look up the existing service using the /pxgrid/control/ServiceLookup endpoint.
- B. Register the service using the /pxgrid/control/ServiceRegister endpoint.
- C. Configure the service using the /pxgrid/ise/config/profiler endpoint.
- D. Expose the service using the /pxgrid/ise/pubsub endpoint.
Answer:
D
Question 8
Which query parameter is required when using the reporting API of Cisco Security Management
Appliances?
- A. device_type
- B. query_type
- C. filterValue
- D. startDate + endDate
Answer:
D
Question 9
Refer to the exhibit.
What is the purpose of the API represented by this URL?
- A. Getting or setting intrusion policies in FMC
- B. Creating an intrusion policy in FDM
- C. Updating access policies
- D. Getting the list of intrusion policies configured in FDM
Answer:
D
Question 10
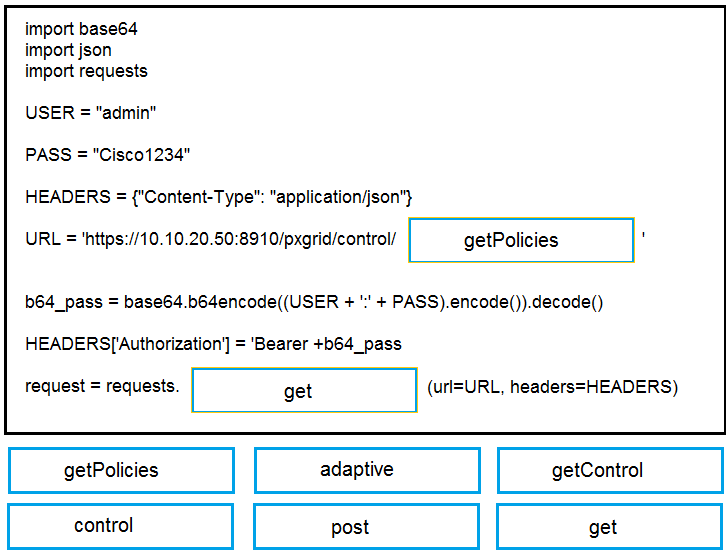
DRAG DROP
Drag and drop the items to complete the pxGrid script to retrieve all Adaptive Network Control
policies. Assume that username, password, and base URL are correct. Not all options are used.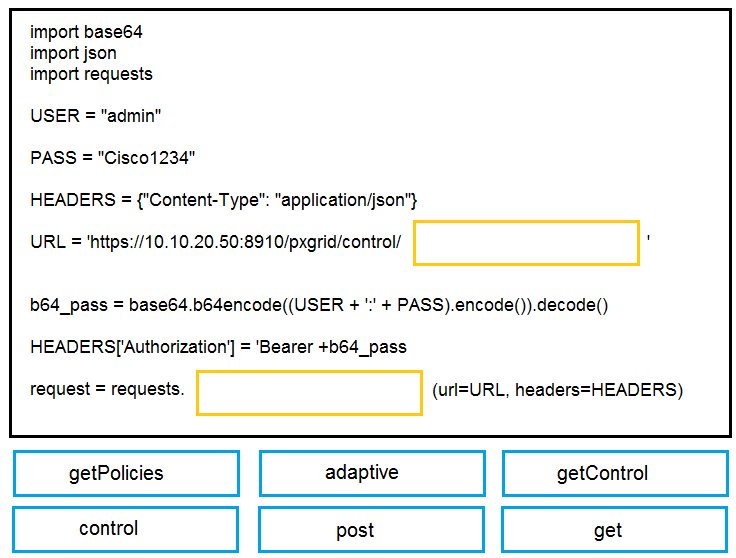
Answer:
Reference:
https://developer.cisco.com/docs/pxgrid/#!retreiving-all-anc-polices/java-sample-code
Question 11
What is the purpose of the snapshot APIs exposed by Cisco Stealthwatch Cloud?
- A. Report on flow data during a customizable time period.
- B. Operate and return alerts discovered from infrastructure observations.
- C. Return current configuration data of Cisco Stealthwatch Cloud infrastructure.
- D. Create snapshots of supported Cisco Stealthwatch Cloud infrastructure.
Answer:
B
Question 12
Refer to the exhibit. A network operator wrote a Python script to retrieve events from Cisco AMP.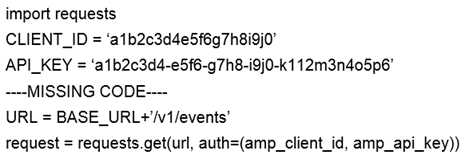
Against which API gateway must the operator make the request?
- A. BASE_URL = “ https://api.amp.cisco.com ”
- B. BASE_URL = “ https://amp.cisco.com/api ”
- C. BASE_URL = “ https://amp.cisco.com/api/ ”
- D. BASE_URL = “ https://api.amp.cisco.com/ ”
Answer:
A
Question 13
Which request searches for a process window in Cisco ThreatGRID that contains the word “secret”?
- A. /api/v2/search/submissions?term=processwindow&title=secret
- B. /api/v2/search/submissions?term=processwindow&q=secret
- C. /api/v2/search/submissions?term=window&title=secret
- D. /api/v2/search/submissions?term=process&q=secret
Answer:
D
Question 14
Which snippet describes the way to create an URL object in Cisco FDM using FDM REST APIs with
curl?
A)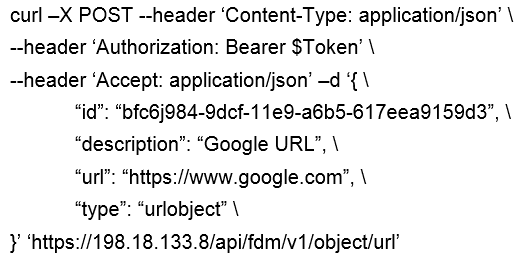
B)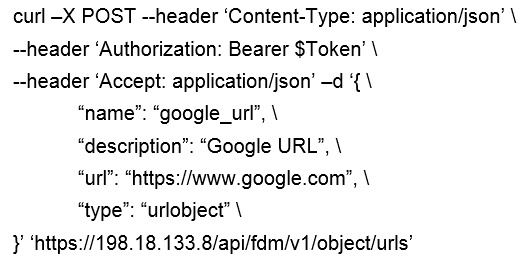
C)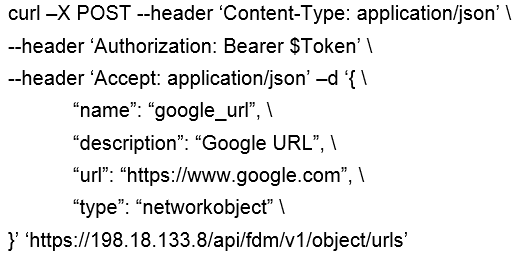
D)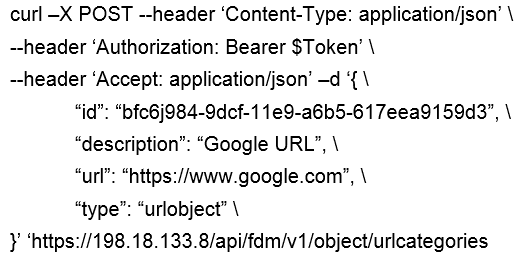
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
B
Question 15
Which API is used to query if the domain “example.com” has been flagged as malicious by the Cisco
Security Labs team?
A.
https://s-platform.api.opendns.com/1.0/events?example.com
B.
https://investigate.api.umbrella.com/domains/categorization/example.com
C.
https://investigate.api.umbrella.com/domains/volume/example.com
D.
https://s-platform.api.opendns.com/1.0/domains?example.com
Answer:
B