cisco 300-730 Exam Questions
Questions for the 300-730 were updated on : Jan 20 ,2026
Page 1 out of 12. Viewing questions 1-15 out of 175
Question 1
An engineer must investigate a connectivity issue and decides to use the packet capture feature on
Cisco FTD. The goal is to see the real packet going through the Cisco FTD device and see Snort
detection actions as a part of the output. After the capture-traffic command is issued, only the
packets are displayed. Which action resolves this issue?
- A. Specify the trace using the -T option after the capture-traffic command
- B. Perform the trace within the Cisco FMC GUI instead of the Cisco FMC CLI
- C. Use the verbose option as a part of the capture-traffic command
- D. Use the capture command and specify the trace option to get the required information
Answer:
A
Explanation:
The correct answer is A. Specify the trace using the -T option after the capture-traffic command.
According to the document
Use Firepower Threat Defense Captures and Packet Tracer
, the capture-
traffic command allows you to capture packets on the Snort engine domain of the FTD device.
However, by default, it only shows the packet headers and does not include the Snort detection
actions. To see the Snort detection actions, you need to use the -T option, which enables tracing. For
example:
capture-traffic -T
This will show the packet headers along with the Snort verdicts, such as allow, block, or replace.
You
can also use other options to filter or save the capture output1
.
B. Performing the trace within the Cisco FMC GUI instead of the Cisco FMC CLI is not a valid option,
because the FMC GUI does not support packet capture or tracing on the FTD device.
You can only use
the FMC GUI to view and export captures that are taken on the FTD CLI1
.
C. Using the verbose option as a part of the capture-traffic command is not a valid option, because
there is no verbose option for this command.
The verbose option is only available for the capture
command, which is used to capture packets on the LINA engine domain of the FTD device1
.
D. Using the capture command and specifying the trace option to get the required information is not
a valid option, because the capture command does not have a trace option. The capture command
allows you to capture packets on the LINA engine domain of the FTD device, but it does not show the
Snort detection actions.
The trace option is only available for the packet-tracer command, which is
used to simulate a packet going through the FTD device and show its processing steps1
.
Question 2
A network administrator wants to block traffic to a known malware site at https:/www.badsite.com
and all subdomains while ensuring no packets from any internal client are sent to that site. Which
type of policy must the network administrator use to accomplish this goal?
- A. Access Control policy with URL filtering
- B. Prefilter policy
- C. DNS policy
- D. SSL policy
Answer:
A
Explanation:
The correct answer is A. Access Control policy with URL filtering. An Access Control policy is a type of
policy that allows you to control how traffic is handled on your network based on various criteria,
such as source and destination IP addresses, ports, protocols, applications, users, and URLs. URL
filtering is a feature that enables you to block or allow traffic based on the URL category or
reputation of the website. You can create custom URL objects to specify the exact URLs or domains
that you want to block or allow. For example, you can create a URL object for
https:/www.badsite.com and set it to block.
This will prevent any traffic from reaching that site and
any subdomains under it12
.
B. Prefilter policy is a type of policy that allows you to perform fast actions on traffic before it reaches
the Access Control policy. You can use prefilter rules to drop, fastpath, or trust traffic based on simple
criteria, such as IP addresses or ports.
However, prefilter rules do not support URL filtering, so you
cannot use them to block traffic based on the website domain3
.
C. DNS policy is a type of policy that allows you to inspect and modify DNS requests and responses on
your network. You can use DNS rules to block, monitor, or sinkhole DNS queries based on the
requested domain name or the response IP address. However, DNS policy does not prevent packets
from being sent to the malicious site; it only prevents the DNS resolution of the domain name. A
client could still access the site if they know the IP address or use an alternative DNS server.
D. SSL policy is a type of policy that allows you to decrypt and inspect encrypted traffic on your
network. You can use SSL rules to determine which traffic to decrypt based on various criteria, such
as certificate attributes, cipher suites, or URL categories. However, SSL policy does not block traffic; it
only decrypts it for further inspection by other policies.
Question 3
A network administrator is deploying a Cisco IPS appliance and needs it to operate initially without
affecting traffic flows. It must also collect data to provide a baseline of unwanted traffic before being
reconfigured to drop it. Which Cisco IPS mode meets these requirements?
- A. failsafe
- B. inline tap
- C. promiscuous
- D. bypass
Answer:
C
Explanation:
The correct answer is C. promiscuous mode. In promiscuous mode, the Cisco IPS appliance operates
as a passive device that monitors a copy of the network traffic and analyzes it for malicious activity.
The appliance does not affect the traffic flow, but it can generate alerts, logs, and reports based on
the configured security policy.
Promiscuous mode is useful for initial deployment and baseline
analysis, as well as for monitoring low-risk segments of the network12
.
A. failsafe mode is a feature that determines how the appliance behaves when a hardware or
software failure occurs.
It does not affect the normal traffic flow or analysis3
. B. inline tap mode is a
variation of inline mode that allows the appliance to pass traffic without inspection in case of a
power failure or a software crash.
It does not allow the appliance to collect data without affecting
traffic4
. D. bypass mode is a feature that enables the appliance to bypass traffic without inspection
when it is overloaded or under maintenance. It does not allow the appliance to analyze traffic and
generate alerts.
:
How the Sensor Functions 2
:
Cisco ASA IPS Module Quick Start Guide 3: Failsafe Mode 4
:
Inline Tap
Mode
: Bypass Mode
Question 4
An engineer is creating an URL object on Cisco FMC. How must it be configured so that the object will
match for HTTPS traffic in an access control policy?
- A. Specify the protocol to match (HTTP or HTTPS).
- B. Use the FQDN including the subdomain for the website.
- C. Use the subject common name from the website certificate.
- D. Define the path to the individual webpage that uses HTTPS.
Answer:
B
Explanation:
Use the FQDN including the subdomain for the website.
According to the Firepower Management
Center Configuration Guide, Version 6.61
, when you create a URL object, you must use the fully
qualified domain name (FQDN) of the website, including any subdomains, and omit the protocol
prefix (HTTP or HTTPS). For example, to match www.example.com, you must enter
www.example.com as the URL object value, not http://www.example.com or
https://www.example.com. The system automatically matches both HTTP and HTTPS traffic for the
same FQDN. Specifying the protocol to match (HTTP or HTTPS) is not required and will result in an
invalid URL object. Using the subject common name from the website certificate or defining the path
to the individual webpage that uses HTTPS are not supported options for URL objects.
Question 5
A network engineer must expand a company's Cisco AnyConnect solution. Currently, a Cisco ASA is
set up in North America and another will be installed in Europe with a different IP address. Users
should connect to the ASA that has the lowest Round Trip Time from their network location as
measured by the AnyConnect client. Which solution must be implemented to meet this
requirement?
- A. VPN Load Balancing
- B. IP SLA
- C. DNS Load Balancing
- D. Optimal Gateway Selection
Answer:
D
Explanation:
Optimal Gateway Selection (OGS). OGS is a feature that can be used in order to determine which
gateway has the lowest Round Trip Time (RTT) and connect to that gateway. One can use the OGS
feature in order to minimize latency for Internet traffic without user intervention. With OGS, Cisco
AnyConnect Secure Mobility Client (AnyConnect) identifies and selects which secure gateway is best
for connection or reconnection. OGS begins upon first connection or upon a reconnection at least
four hours after the previous disconnection.
Question 6
Which clientless SSLVPN supported feature works when the http-only-cookie command is enabled?
- A. Citrix load balancer
- B. port reflector
- C. Java plug-ins
- D. script browser
Answer:
D
Explanation:
https://www.cisco.com/c/en/us/td/docs/security/asa/asa94/config-guides/asdm74/vpn/asdm-74-vpn-config/webvpn-troubleshooting.html
The following Clientless SSL VPN features will not work when the http-only-cookie command is
enabled:
• Java plug-ins
• Java rewriter
• Port forwarding
• File browser
• Sharepoint features that require desktop applications (for example, MS Office applications)
• AnyConnect Web launch
• Citrix Receiver, XenDesktop, and Xenon
• Other non-browser-based and browser plugin-based applications
Question 7
An administrator is deciding which authentication protocol should be implemented for their
upcoming Cisco AnyConnect deployment. A list of the security requirements from upper
management are: the ability to force AnyConnect users to use complex passwords such as
C1$c0451035084!, warn users a few days before their password expires, and allow users to change
their password during a remote access session. Which authentication protocol must be used to meet
these requirements?
- A. LDAPS
- B. RADIUS
- C. Kerberos
- D. TACACS+
Answer:
A
Explanation:
To enforce complex passwords—for example, to require that a password contain upper- and
lowercase letters, numbers, and special characters—enter the password-management command in
tunnel-group general-attributes configuration mode on the ASA and perform the following steps
under Active Directory.
https://www.cisco.com/c/en/us/td/docs/security/asa/asa97/configuration/vpn/asa-97-vpn-config/vpn-groups.html
Question 8
A network administrator wants the Cisco ASA to automatically start downloading the Cisco
AnyConnect client without prompting the user to select between WebVPN or AnyConnect. Which
command accomplishes this task?
- A. anyconnect ssl df-bit-ignore enable
- B. anyconnect ask none default anyconnect
- C. anyconnect ask enable default anyconnect
- D. anyconnect modules value default
Answer:
B
Explanation:
https://networklessons.com/cisco/asa-firewall/cisco-asa-anyconnect-remote-access-
vpn#:~:text=The%20anyconnect%20ask%20command%20specifies,of%20the%20anyconnect%20clie
nt%20automatically
.
Question 9
DRAG DROP
-
Drag and drop the GET VPN components from the left onto the correct descriptions on the right.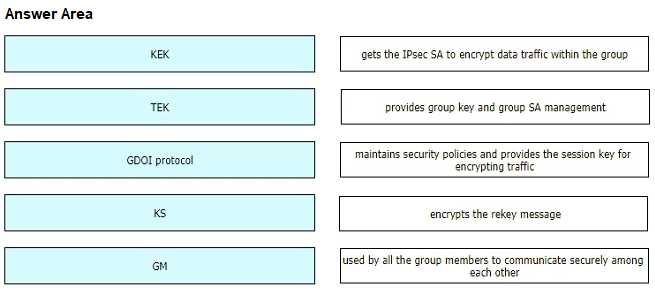
Answer:
None
Explanation:
KEK - Encrypts the rekey message
TEK - Used by all the group members to communicate securely among each other
"The TEK becomes the IPsec SA with which the group members within the same group
communicate. The KEK encrypts the rekey message."
GDOI protocol - Provides group key and group AS management
"DGOI is defined as the Internet Security Association Key Management Protocol (ISAKMP) Domain of
Interpretation (DOI) for group key management."
KS - Maintains security policies and provides the session key for encrypting traffic
"The responsibilities of the key server include maintaining the policy and creating and maintaining
the keys for the group. When a group member registers, the key server downloads this policy and
the keys to the group member. The key server also rekeys the group before existing keys expire."
GM - Gets the IPSec SA to encrypto data traffic within the group
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_conn_getvpn/configuration/xe-3s/sec-get-vpn-xe-3s-book/sec-get-vpn.html#GUID-C8F2200D-C50E-408B-966F-249EC70AADD0
Question 10
Which two protocols does DMVPN leverage to build dynamic VPNs to multiple destinations? (Choose
two.)
- A. IKEv2
- B. NHRP
- C. mGRE
- D. mBGP
- E. GDOI
Answer:
BC
Question 11
Refer to the exhibit.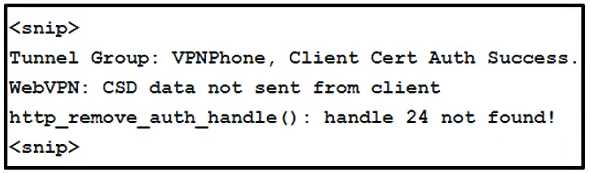
A network administrator is setting up a phone VPN on a Cisco AS
- A. Enable web-deploy of the posture module so that the module can be downloaded from the Cisco ASA to an IP phone.
- B. Configure the Cisco ASA to present an RSA certificate to the phone for authentication.
- C. Disable Cisco Secure Desktop under the connection profile VPNPhone.
- D. Install the posture module on the Cisco ASA.
Answer:
C
Explanation:
CSD and IP phones: Currently, IP phones do not support Cisco Secure Desktop (CSD) and do not
connect when CSD is enabled for the tunnel group or globally in the ASA.
Question 12
DRAG DROP
Drag and drop the GETVPN components from the left onto the descriptions on the right.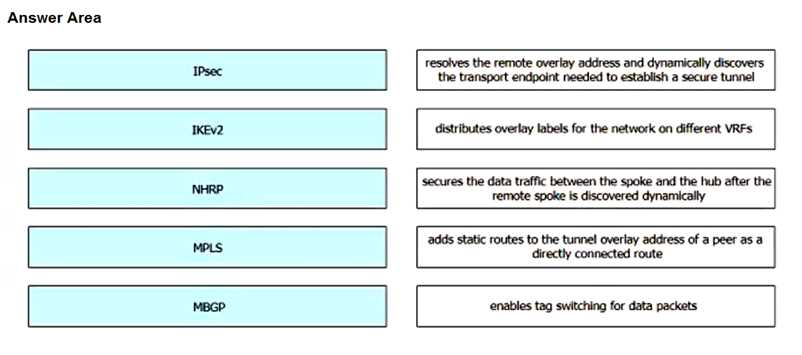
Answer:
None
Explanation:
IPSec: Secures the data traffic,..
IKEv2: Adds statics routes,..
NHRP: Resolves the remote,..
MPLS: Enables tag switching for data,..
MPBGP: Distributes overlay,..
Question 13
An engineer is implementing the FlexVPN solution on a Cisco IOS router. The router must only
terminate VPN requests and must not initiate them. Additionally, the interface must support VPNs
from other routers and Cisco AnyConnect connections. Which interface type must be configured to
meet these requirements?
- A. point-to-point GRE tunnel interface
- B. multipoint GRE tunnel interface
- C. static virtual tunnel interface
- D. virtual template interface
Answer:
D
Explanation:
The correct interface type to meet these requirements is the virtual template interface. This
interface allows for the creation of multiple virtual access interfaces, which can be used for various
types of remote access VPN connections, including site-to-site and AnyConnect VPNs. The virtual
template interface can be configured to terminate VPN requests from other routers and allow for
dynamic creation of VPN sessions, while also supporting AnyConnect VPN connections.
Question 14
Which command must be configured on the tunnel interface of a FlexVPN spoke to receive a dynamic
IP address from the hub?
- A. ip address negotiated
- B. ip unnumbered
- C. ip address dhcp
- D. ip address pool
Answer:
A
Explanation:
https://integratingit.wordpress.com/2018/03/31/configuring-flexvpn-external-aaa-with-radius/
interface Tunnel0
ip address negotiated
tunnel source GigabitEthernet1
tunnel mode ipsec ipv4
tunnel destination 1.1.1.5
tunnel protection ipsec profile IPSEC_PROFILE
Question 15
An administrator is setting up Cisco AnyConnect on a Cisco ASA with the requirement that
AnyConnect automatically establishes a VPN when a company-owned laptop is connected to the
internet outside of the corporate network. Which configuration meets these requirements?
- A. SBL with user certificate authentication
- B. TND with machine certificate authentication
- C. SBL with machine certificate authentication
- D. TND with user certificate authentication
Answer:
B
Explanation:
Trusted Network Detection (TND) gives you the ability to have AnyConnect automatically disconnect
a VPN connection when the user is inside the corporate network (the trusted network) and start the
VPN connection when the user is outside the corporate network (the untrusted network).
https://www.cisco.com/c/en/us/td/docs/security/vpn_client/anyconnect/anyconnect41/administration/guide/b_AnyConnect_Administrator_Guide_4-1/configure-vpn.html#id_100236