cisco 300-725 Exam Questions
Questions for the 300-725 were updated on : Feb 18 ,2026
Page 1 out of 4. Viewing questions 1-15 out of 60
Question 1
What is the primary benefit of using Cisco Advanced Web Security Reporting?
- A. ability to see the malicious activity of a user
- B. L4TM report with client-malware risk
- C. centralized and granular reporting
- D. access to a day report with historical data
Answer:
B
Reference:
https://www.cisco.com/c/en/us/products/collateral/security/web-security-appliance/datasheet_c78-729104.html
Question 2
When an access policy is created, what is the default option for the Application Settings?
- A. Use Global Policy Applications Settings
- B. Define the Applications Custom Setting
- C. Set all applications to Block
- D. Set all applications to Monitor
Answer:
B
Reference:
https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-7/user_guide/b_WSA_UserGuide_11_7/b_WSA_UserGuide_11_7_chapter_01111.html
Question 3
What is a benefit of integrating Cisco WSA with TrustSec in ISE?
- A. The policy trace tool can be used to match access policies using specific SGT
- B. Traffic of authenticated users who use 802.1x can be tagged with SGT to identification profiles in a Cisco WSA
- C. ISE can block authentication for users who generate multiple sessions using suspect TCP ports
- D. Users in a specific SGT can be denied access to certain social websites.
Answer:
D
Reference:
https://www.cisco.com/c/en/us/td/docs/security/ise/1-3/ISE-WSAIntegrationDoc/b_ISE-WSAIntegration.html
Question 4
Which port is configured in a browser to use the Cisco WSA web proxy with default settings?
B. 8443
C. 8021
D. 3128
Answer:
D
Reference:
https://www.cisco.com/c/dam/en/us/td/docs/solutions/CVD/Aug2013/CVD
-
WebSecurityUsingCiscoWSADesignGuide-AUG13.pdf (16)
Question 5
Which two log types does the Cisco WSA provide to troubleshoot Cisco data security and external
data loss prevention policies? (Choose two.)
- A. upload data
- B. data security
- C. default proxy
- D. data access
- E. external data
Answer:
CE
Reference:
https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-0/user_guide/b_WSA_UserGuide/b_WSA_UserGuide_chapter_010011.html
Question 6
Which type of certificate must be installed on a Cisco WSA for HTTPS inspection?
- A. server
- B. client
- C. root
- D. wildcard
Answer:
C
Reference:
https://www.cisco.com/c/en/us/support/docs/security/web-security-appliance/117792-technote-wsa-00.html
Question 7
What is the purpose of using AMP file analysis on a Cisco WSA to continuously evaluate emerging
threats?
- A. to take appropriate action on new files that enter the network
- B. to remove files from quarantine by stopping their retention period
- C. to notify you of files that are determined to be threats after they have entered your network
- D. to send all files downloaded through the Cisco WSA to the AMP cloud
Answer:
C
Reference:
https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-5/user_guide/b_WSA_UserGuide_11_5_1/b_WSA_UserGuide_11_5_1_chapter_01110.html
Question 8
Which two configuration options can be configured when invalid certificates are processed with the
HTTPS proxy on WSA enabled? (Choose two.)
- A. allow
- B. monitor
- C. drop
- D. block
- E. redirect
Answer:
BC
Reference:
https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-7/user_guide/
Question 9
What is needed to enable an HTTPS proxy?
- A. self-signed server certificate
- B. trusted third-party CA signed root certificate
- C. self-signed CSR
- D. self-signed root certificate
Answer:
C
Reference:
https://community.cisco.com/t5/web-security/cisco-wsa-https-proxy-certificate-issue/td-p/3019392
Question 10
How does dynamic content analysis improve URL categorization?
- A. It analyzes content based on cached destination content
- B. It adds intelligence to detect categories by analyzing responses
- C. It can be used as the only URL analysis method
- D. It analyzes content of categorized URL to tune decisions and correct categorization errors
Answer:
D
Reference:
https://www.cisco.com/c/en/us/support/docs/security/web-security-appliance/118063-qanda-wsa-00.html
Question 11
Which two caching modes are available in the Cisco WSA? (Choose two.)
- A. active cache
- B. all cache
- C. aggressive cache
- D. safe cache
- E. no cache
Answer:
CD
Reference:
https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-5/user_guide/b_WSA_UserGuide_11_5_1/b_WSA_UserGuide_11_5_1_chapter_0100.html#task_1214899
Question 12
An administrator wants to restrict file uploads to Facebook using the AVC feature.
Under which two actions must the administrator apply this restriction to an access policy? (Choose
two.)
- A. Monitor Facebook General
- B. Monitor Social Networking
- C. Monitor Facebook Photos and Videos
- D. Monitor Facebook Messages and Chat
- E. Monitor Facebook Application
Answer:
AC
Reference:
https://www.cisco.com/c/en/us/products/collateral/security/web-security-appliance/datasheet-c78-741272.html
Question 13
DRAG DROP
Drag and drop the access policy options from the left onto the correct descriptions on the right.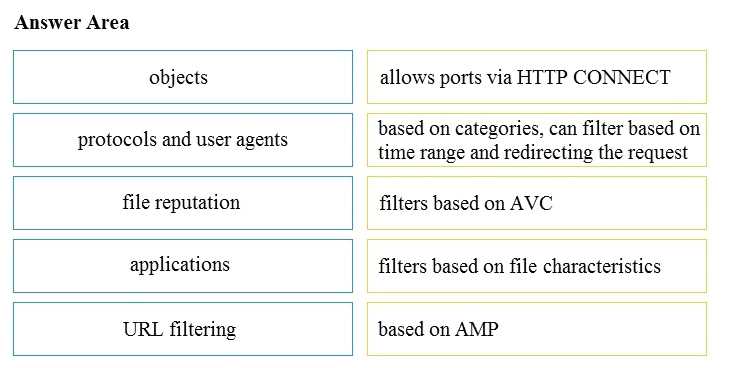
Answer:
Reference:
https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-0/user_guide/b_WSA_UserGuide/
b_WSA_UserGuide_chapter_01101.pdf (10)
Question 14
Which type of FTP proxy does the Cisco WSA support?
- A. non-native FTP
- B. FTP over UDP tunneling
- C. FTP over HTTP
- D. hybrid FTP
Answer:
C
Reference:
https://www.cisco.com/c/en/us/support/docs/security/web-security-appliance/117984-qanda-wsa-00.html
Question 15
What is the default action when a new custom category is created and added to an access policy?
- A. monitor
- B. allow
- C. block
- D. decrypt
Answer:
A
Reference:
https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-7/user_guide/