cisco 300-715 Exam Questions
Questions for the 300-715 were updated on : Jul 20 ,2024
Page 1 out of 6. Viewing questions 1-15 out of 82
Question 1 Topic 1
Topic 1
Which personas can a Cisco ISE node assume?
- A. policy service, gatekeeping, and monitoring
- B. administration, monitoring, and gatekeeping
- C. administration, policy service, and monitoring
- D. administration, policy service, gatekeeping
Answer:
C
Explanation:
Reference: https://www.cisco.com/en/US/docs/security/ise/1.0/user_guide/ise10_dis_deploy.html
Question 2 Topic 1
Topic 1
What occurs when a Cisco ISE distributed deployment has two nodes and the secondary node is deregistered?
- A. The secondary node restarts.
- B. The primary node restarts.
- C. Both nodes restart.
- D. The primary node becomes standalone.
Answer:
C
Question 3 Topic 1
Topic 1
DRAG DROP
Drag the steps to configure a Cisco ISE node as a primary administration node from the left into the correct order on the
right.
Select and Place:
Answer:
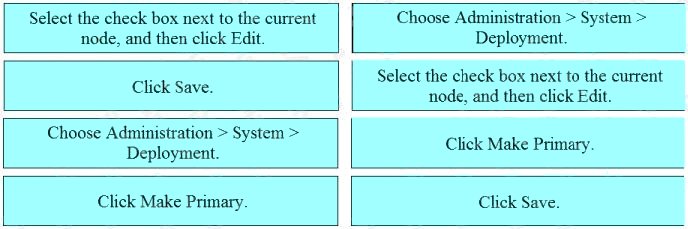
Explanation:
Reference: https://www.cisco.com/en/US/docs/security/ise/1.0/user_guide/ise10_dis_deploy.html
Question 4 Topic 1
Topic 1
Which two features are available when the primary admin node is down and the secondary admin node has not been
promoted? (Choose two.)
- A. new AD user 802.1X authentication
- B. hotspot
- C. posture
- D. guest AUP
- E. BYOD
Answer:
B D
Question 5 Topic 1
Topic 1
Which supplicant(s) and server(s) are capable of supporting EAP-CHAINING?
- A. Cisco Secure Services Client and Cisco Access Control Server
- B. Cisco AnyConnect NAM and Cisco Identity Service Engine
- C. Cisco AnyConnect NAM and Cisco Access Control Server
- D. Windows Native Supplicant and Cisco Identity Service Engine
Answer:
B
Explanation:
Reference: https://www.cisco.com/c/en/us/support/docs/wireless-mobility/eap-fast/200322-Understanding-EAP-FAST-and-
Chaining-imp.html
Question 6 Topic 1
Topic 1
What is a requirement for Feed Service to work?
- A. TCP port 8080 must be opened between Cisco ISE and the feed server.
- B. Cisco ISE has access to an internal server to download feed update.
- C. Cisco ISE has a base license.
- D. Cisco ISE has Internet access to download feed update.
Answer:
B
Question 7 Topic 1
Topic 1
What is a method for transporting security group tags throughout the network?
- A. by embedding the security group tag in the 802.1Q header
- B. by the Security Group Tag Exchange Protocol
- C. by enabling 802.1AE on every network device
- D. by embedding the security group tag in the IP header
Answer:
B
Question 8 Topic 1
Topic 1
An engineer is configuring a virtual Cisco ISE deployment and needs each persona to be on a different node.
Which persona should be configured with the largest amount of storage in this environment?
- A. Monitoring and Troubleshooting
- B. Policy Services
- C. Primary Administration
- D. Platform Exchange Grid
Answer:
A
Question 9 Topic 1
Topic 1
In a standalone Cisco ISE deployment, which two personas are configured on a node? (Choose two.)
- A. subscriber
- B. primary
- C. administration
- D. publisher
- E. policy service
Answer:
C E
Question 10 Topic 1
Topic 1
A network engineer must enforce access control using special tags, without re-engineering the network design.
Which feature should be configured to achieve this in a scalable manner?
- A. RBAC
- B. dACL
- C. SGT
- D. VLAN
Answer:
C
Explanation:
Reference: https://www.cisco.com/c/dam/en/us/solutions/collateral/enterprise-networks/trustsec/branch-segmentation.pdf
Question 11 Topic 1
Topic 1
A network engineer is configuring a network device that needs to filter traffic based on security group tags using a security
policy on a routed interface.
Which command should be used to accomplish this task?
- A. cts role-based policy priority-static
- B. cts cache enable
- C. cts authorization list
- D. cts role-based enforcement
Answer:
D
Question 12 Topic 1
Topic 1
In a Cisco ISE split deployment model, which load is split between the nodes?
A. log collection
B. device admission
C. AAA
D. network admission
Answer:
A
Topic 2, Policy Enforcement
Question 13 Topic 2
Topic 2
How is policy services node redundancy achieved in a deployment?
- A. by creating a node group
- B. by deploying both primary and secondary node
- C. by enabling VIP
- D. by utilizing RADIUS server list on the NAD
Answer:
B
Question 14 Topic 2
Topic 2
Which two fields are available when creating an endpoint on the context visibility page of Cisco ISE? (Choose two.)
- A. Security Group Tag
- B. Endpoint Family
- C. Policy Assignment
- D. Identity Group Assignment
- E. IP Address
Answer:
C D
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/ise/2-
2/admin_guide/b_ise_admin_guide_22/b_ise_admin_guide_22_chapter_010101.html
Question 15 Topic 2
Topic 2
In which two ways can users and endpoints be classified for TrustSec? (Choose two.)
- A. VLAN
- B. dynamic
- C. QoS
- D. SGACL
- E. SXP
Answer:
A D