cisco 300-710 Exam Questions
Questions for the 300-710 were updated on : Feb 18 ,2026
Page 1 out of 26. Viewing questions 1-15 out of 376
Question 1
DRAG DROP
An engineer must configure high availability on two Cisco Secure Firewall Threat Defense appliances.
Drag and drop the configuration steps from the left into the sequence on the right.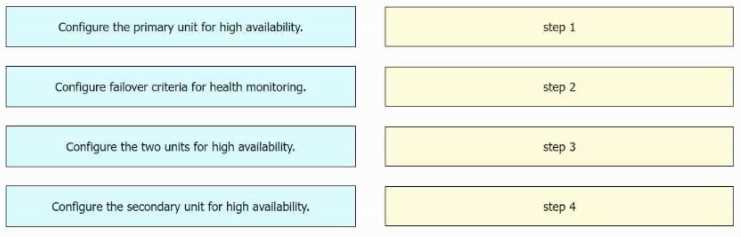
Answer:
None
Explanation:
Step 1(Configure the primary unit for high availability),
Step 2(Configure the secondary unit for high availability),
Step 3(Configure the two units for high availability),
Step 4(Configure failover criteria for health monitoring)
Question 2
After a network security breach, an engineer must strengthen the security of the corporate network.
Upper management must be regularly updated with a high-level overview of any
occurring network threats. Which access must the engineer provide upper management to view the
required data from Cisco Secure Firewall Management Center?
- A. Analysis > Status with a sliding time window of one day
- B. Events by priority and classification and set a sliding time window of one day
- C. Reports with a daily recurring task that generates based on the network risk report template
- D. Security Intelligence Statistics dashboard set to Show the Last option to one day
Answer:
C
Question 3
An engineer must permit SSH on the inside interface of a Cisco Secure Firewall Threat Defense
device. SSH is currently permitted only on the management interface. Which type of policy
must the engineer configure?
- A. platform policy
- B. access control policy
- C. NAT policy
- D. intrusion policy
Answer:
A
Question 4
An engineer must integrate a third-party security intelligence feed with Cisco Secure Firewall
Management Center. Secure Firewall Management Center is running Version 6.2.3 and has 8
GB of memory. Which two actions must be taken to implement Threat Intelligence Director? (Choose
two.)
- A. Enable REST API access.
- B. Add a TAXII server.
- C. Add the URL of the TAXII server.
- D. Upgrade to version 6.6.
- E. Add 7 GB of memory.
Answer:
A, E
Question 5
A VPN administrator converted an instance of Cisco Secure Firewall Threat Defense, which is
managed by Cisco Secure Firewall Management Center, from using LDAP to LDAPS for
remote access VPN authentication. Which certificate must be added to allow for remote users to
authenticate over the VPN?
- A. LDAPS server certificate must be added to Secure Firewall Management Center realms.
- B. Secure Firewall Management Center certificate must be added to the LDAPS server.
- C. LDAPS server certificate must be added to Secure Firewall Threat Defense.
- D. Secure Firewall Threat Defense certificate must be added to the LDAPS server.
Answer:
C
Question 6
A network engineer wants to disable the HTTP response page and interactive blocking of the entire
access control policy in Cisco Secure Firewall Management Center. What must be
selected in Block Response Page and Interactive Block Response Page?
- A. Custom
- B. View
- C. System
- D. None
Answer:
D
Question 7
Refer to the exhibit.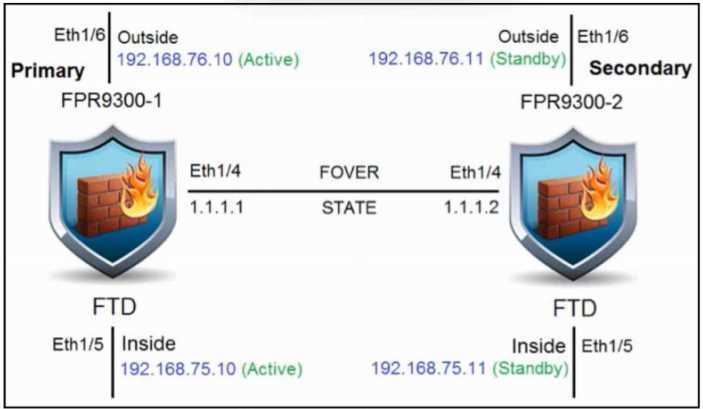
Refer to the exhibit. An engineer is configuring a high-availability solution that has the hardware
devices and software versions:
two Cisco Secure Firewall 9300 Security Appliances with FXOS SW 2.0(1.23)
software Cisco Secure Firewall Threat Defense 6.0.1.1 (build 1023) on both appliances
one Cisco Secure Firewall Management Center with SW 6.0.1.1 (build 1023)
Which condition must be met to complete the high-availability configuration?
- A. DHCP must be configured on at least one firewall interface.
- B. The version numbers must have the same patch number.
- C. Both firewalls must have the same number of interfaces.
- D. Both firewalls must be in transparent mode.
Answer:
C
Question 8
Which feature sets up multiple interfaces on a Cisco Secure Firewall Threat Defense to be on the
same subnet?
- A. EtherChannel
- B. SVI
- C. BVI
- D. security levels
Answer:
C
Question 9
An engineer is setting up a new Cisco Secure Firewall Threat Defense appliance to replace the current
firewall. The company requests that inline sets be used and that when one interface in
an inline set goes down, the second interface in the inline set goes down. What must the engineer
configure to meet the deployment requirements?
- A. strict TCP enforcement
- B. propagate link state
- C. Snort fail open
- D. inline tap mode
Answer:
C
Question 10
An engineer must investigate a connectivity issue by using Cisco Secure Firewall Management Center
to access the Packet Capture feature on a Cisco Secure Firewall Threat Defense
device. The engineer must see a real packet going through the Secure Firewall Threat Defense device
and the Snort detection actions. While reviewing the packet capture, the engineer
discovers that the Snort detection actions are missing. Which action must the engineer take to
resolve the issue?
- A. Specify the packet size.
- B. Specify the buffer size.
- C. Enable the Continuous Capture option.
- D. Enable the Trace option.
Answer:
D
Question 11
What is the role of realms in the Cisco ISE and Cisco Secure Firewall Management Center
integration?
- A. TACACS+ database
- B. AD definition
- C. Cisco Secure Firewall VDC
- D. Cisco ISE context
- E. (Option not provided – please confirm or provide)
Answer:
C
Question 12
An engineer is integrating Cisco Secure Endpoint with Cisco Secure Firewall Management Center in
high availability mode. Malware events detected by Secure Endpoint must also be
received by Secure Firewall Management Center and public cloud services are used. Which two
configurations must be selected on both high availability peers independently? (Choose two.)
- A. internet connection
- B. Smart Software Manager Satellite
- C. Cisco Success Network
- D. security group tag
- E. Secure Endpoint Cloud Connection
Answer:
A, E
Question 13
Refer to the exhibit.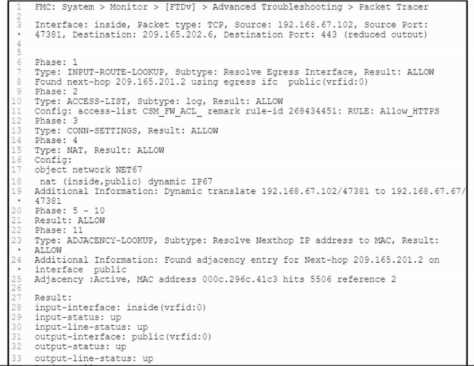
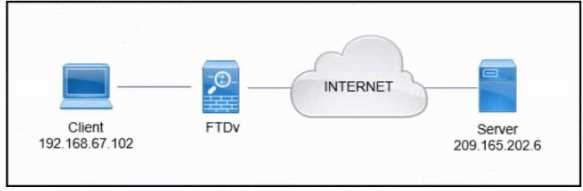
Refer to the exhibit. A client that has IP address 192.168.67.102 reports issues when connecting to a
remote server. Based on the topology and output of packet tracer tool, which action resolves the
connectivity issue?
- A. Add the route to the destination.
- B. Unblock the access rule on FTDv.
- C. Restart the client-side application.
- D. Reconfigure NAT on FTDv.
Answer:
D
Question 14
An engineer must perform a packet capture on a Cisco Secure Firewall Threat Defense device to
confirm the MAC address of the host using IP address 192.168.100.100 while troubleshooting an ARP
issue. What is the correct tcpdump command syntax to ensure that the MAC address appears in the
packet capture output?
- A. -w capture.pcap -s 1518 host 192.168.100.100 mac
- B. -nm src 192.168.100.100
- C. -w capture.pcap -s 1518 host 192.168.100.100 ether
- D. -ne src 192.168.100.100
Answer:
D
Question 15
An engineer must configure an inline set on a Cisco Secure IPS by using the Cisco Secure Firewall
Management Center. The inline set must make a copy of each packet before analyzing the packet and
block any connections that do not complete the three-way handshake. These configurations have
been performed already:
Select and enable the interfaces that will be added to the inline set.
Configure the speed and duplex.
Configure the inline set and add the interfaces to the inline set.
Which action completes the task?
- A. Set Tap Mode to Inline.
- B. Configure Snort Fail Open.
- C. Configure Link State Propagation.
- D. Implement Strict TCP Enforcement.
Answer:
D