cisco 300-620 Exam Questions
Questions for the 300-620 were updated on : Feb 27 ,2026
Page 1 out of 17. Viewing questions 1-15 out of 247
Question 1
What is the maximum number of sites connected using spine back-to-back with a direct link in a
Cisco ACI Multi-Site fabric?
- A. 2
- B. 3
- C. 4
- D. 5
Answer:
A
Explanation:
In a Cisco ACI Multi-Site setup, back-to-back spine connectivity is limited to a direct connection
between two sites. This design simplifies inter-site communication by avoiding the need for an
intermediate Inter-Pod Network (IPN) or Multi-Site Orchestrator.
Question 2
Refer to the exhibit.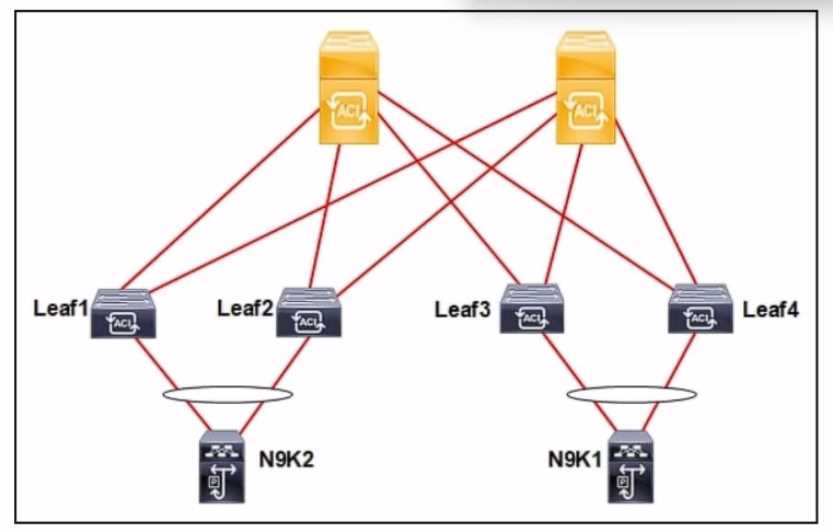
Refer to the exhibit. An engineer connects a Cisco ACI fabric to two different Cisco Nexus 9000 Series
Switches. The fabric must be configured to ensure a loop-free topology and N9K1 be configured as
the root bridge for VLAN 10. Which action meets these requirements?
- A. Enable STP on ports between the leaf and spine.
- B. Activate MCP on ports between the leaf and Nexus 9000 Series Switches.
- C. Enable Cisco Discovery Protocol on ports between the leaf and spine.
- D. Set BPDU Guard on ports between the leaf and Nexus 9000 Series Switches.
Answer:
B
Question 3
A Cisco ACI fabric is integrated with a Cisco ASA firewall using a service graph under the tenant called
Operations. The fabric must permit the firewall used on tenant Operations to be referenced by the
tenant called Management. Which export action must be used to accomplish this goal?
- A. Layer4-Layer7 device
- B. router configurations
- C. service graph template
- D. device selection policies
Answer:
A
Explanation:
In Cisco ACI, when a service graph is deployed under one tenant (e.g., Operations) and needs to be
referenced by another tenant (e.g., Management), the Layer 4-Layer 7 (L4-L7) device export action is
used. This allows the firewall or other L4-L7 devices defined in the service graph to be shared across
tenants. By exporting the L4-L7 device, the configuration enables the Management tenant to
reference and use the firewall deployed in the Operations tenant.
Question 4
An engineer needs to avoid loops in the ACI network and needs an ACI leaf switch to error-disable an
interface if the interface receives an ACI-generated packet. Which action meets these requirements?
- A. Enable the Loop Indication by MCP event in the Error Disabled Recovery Policy.
- B. Set Rogue EP Control in the Endpoint Controls Policy.
- C. Uncheck the Loop Protection Action check box in MCP Instance Policy.
- D. Change the default administrative state of the global MCP Instance Policy.
Answer:
D
Explanation:
MisCabling Protocol (MCP) detects loops from external sources (i.e., misbehaving servers, external
networking equipment running STP, etc.) and will err-disable the interface on which ACI receives its
own packet. Enabling this feature is a best practice, and it should be enabled globally and on all
interfaces, regardless of the end device. For MCP to be enabled, you need to have it enabled globally
and on a per-interface basis. While MCP is enabled on all interfaces by default, it is not turned “on”
until you also enable it globally. The global configuration knob for MCP can be enabled by configuring
the global settings here: Fabric > Access Policies > Global Policies > MCP Instance Policy default.
https://www.cisco.com/c/dam/en/us/solutions/collateral/data-center-virtualization/application-
centric-infrastructure/aci-guide-using-mcp-mis-cabling-protocol.pdf
Question 5
Refer to the exhibit.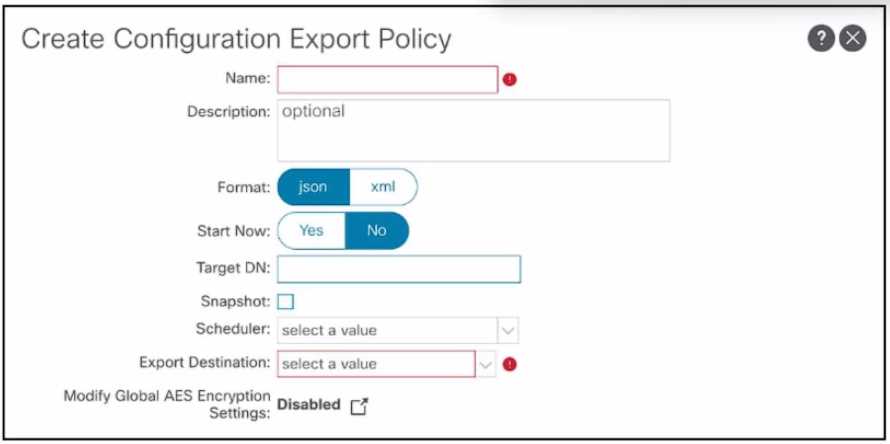
A network engineer must improve the configuration backup process and the configuration restore
process. The current ACI solution is integrated with VMMs and third-y.. L4-L7 devices. The process
requires that no additional information be re-entered when importing the configuration for a fully-
functional state. Which configuration configures the port policy?
- A. Enable the Global AES Encryption Setting.
- B. Select the JSON data format to be used when exporting
- C. Create target DNs for all tenants.
- D. Configure a local snapshot.
Answer:
A
Explanation:
Enabling AES encryption ensures that sensitive data, such as credentials for VMMs and third-party
integrations, is securely encrypted in the backup file. This is essential for a fully functional restore
without requiring re-entry of sensitive details.
Question 6
An engineer implements a configuration backup on the Cisco APIC. The backup job must meet these
requirements:
• The backup must transfer the encrypted data to the remote server.
• The transfer must be resumed if the connection is interrupted.
Which configuration set meets these requirements?
- A. Select protocol HTTP in Create Remote Location. Choose JSON format in Configuration Export Policy.
- B. Select protocol TFTP in Create Remote Location. Choose JSON format in Configuration Export Policy
- C. Select protocol FTP in Create Remote Location. Choose XML format in Configuration Export Policy.
- D. Select protocol SFTP in Create Remote Location. Choose XML format in Configuration Export Policy.
Answer:
D
Question 7
Network engineer configured a Cisco ACI fabric as follows:
• An EPG called EPG-A is created and associated with a VMM domain called North. •The EPG-A is
associated with BD-A and is in an application profile called Apps-A.
• The BD-A is associated with VRF-1 in the Prod tenant.
Which port group must be selected to place VMs in EPG-A?
- A. Prod|VRF-1 |Apps-A|EPG-A
- B. Prod|Business_Apps|BD-A|EPG-A
- C. Prod|Apps-A|North|EPG-A
- D. Prod|Apps-A|EPG-A
Answer:
D
Question 8
Cisco ACI fabric must detect all silent endpoints for the Layer 3 bridge domain. Which actions
accomplish this goal?
- A. Disable Unicast Routing. Enable L2 Unknown Unicast Hardware Proxy.
- B. Disable Unicast Routing. Enable L2 Unknown Unicast Flood.
- C. Enable Unicast Routing. Disable ARP Flooding.
- D. Enable Unicast Routing. Enable ARP Flooding.
Answer:
C
Question 9
How many ARP requests are sent from leaf switches to perform host tracking for local endpoints?
- A. 1
- B. 2
- C. 3
- D. 4
Answer:
A
Question 10
An engineer plans a Cisco ACI firmware upgrade. The ACI fabric consists of three Cisco APIC
controllers, two spine switches, and four leaf switches. Two leaf switches have 1-Gb copper s for bare
metal servers, and the other two leaf switches have 10-Gb SFP ports to connect storage. Which set of
actions accomplishes an upgrade with minimal disruptions?
- A. Upgrade the APIC controllers by selecting the desired firmware and choosing Upgrade Now. Divide the switches into two upgrade groups: spines and leaves. Start the firmware upgrade on the spine upgrade group and then proceed with the leaf upgrade group.
- B. Upgrade the APIC controllers by initiating the upgrade process that uses the most recent uploaded firmware. Divide the switches into three upgrade groups: spines, 1-Gb switches, and 10-Gb switches. Start the firmware upgrade on the spine upgrade group and then proceed with the other two groups.
- C. Upgrade the APIC controllers by selecting the desired firmware and choosing Upgrade Now. Divide the switches into two upgrade groups with one spine, one 1-Gb switch, and one 10-Gb switch per group. Start the firmware upgrade on the first upgrade group and when it finishes, start the second upgrade group.
- D. Upgrade the APIC controllers as a single group by selecting the firmware and choosing Upgrade Now. Divide the switches into four upgrade groups with one switch per group. Start the firmware upgrade on each upgrade group in succession until all four are complete.
Answer:
C
Question 11
Engineer resolves an underlying condition of a fault but notices that the fault was not deleted from
the Faults view. Which two actions must be taken to remove the fault? (Choose two.)
- A. The fault is deleted after the retention interval.
- B. Acknowledge the fault as an administrator.
- C. The raised condition ceases.
- D. The soaking timer expires.
Answer:
AB
Question 12
Refer to the exhibit.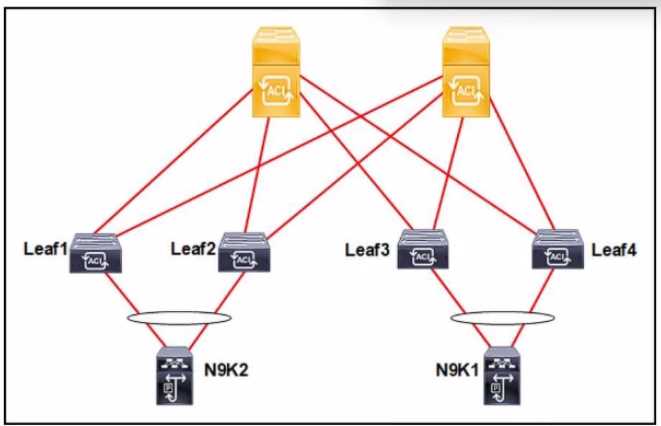
The Cisco ACI fabric is built with L20ut to the N9K1 and N9K2 switches. The switches run the RSTP
protocol. The requirement is for the Cisco ACI fabric to detect 5 from the N9K and for the fabric to be
protected against loops. Which set of actions must be taken to meet the requirements?
- A. Configure the N9K STP link type as point-to-point link. Enable MCP on ACI globally.
- B. Configure the N9K STP link type as a point-to-point Enable MCP on the ACI leaf interfaces.
- C. Configure the N9K STP link type as a shared link. Enable MCP on the ACI leaf interfaces.
- D. Configure the N9K STP link type as a shared link. Enable MCP on ACI globally.
Answer:
D
Question 13
What is the result of selecting the On Demand attribute in the Deploy Immediacy feature during
VMM domain association to an EPG?
- A. The EPG policy is downloaded to the leaf when a hypervisor is connected, and a VM is placed in a port group.
- B. The EPG policy is programmed in the hardware policy CAM only when the first packet is received through the data path.
- C. The EPG policy is programmed in the hardware policy CAM as soon as the policy is downloaded in the leaf software.
- D. The EPG policy is downloaded to the leaf when a hypervisor is attached to a DVS. and CDP or LLDP adjacency is formed.
Answer:
B
Question 14
Refer to the exhibit.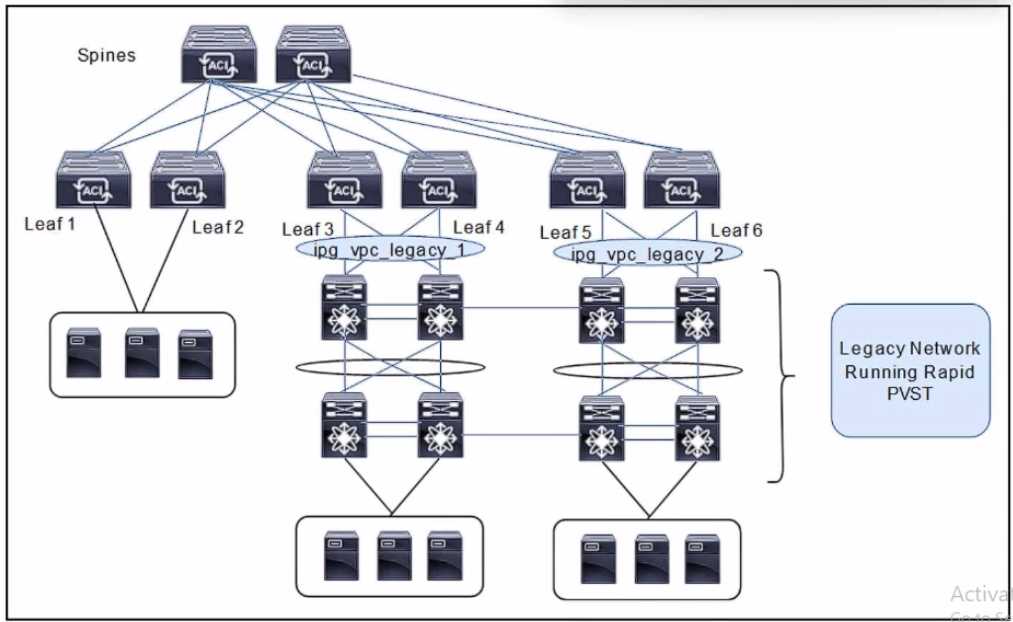
Refer to the exhibit. A client is configuring a new Cisco ACI fabric. All VLANs will be extended during
the migration phase using the VPC connections on leaf switches 3. 4 and leaf switches toward the
legacy network. The migration phase has these requirements;
* If The legacy switches must be able to transfer BPDUs through the ACI fabric.
* If the legacy switches fail to break a loop. Cisco ACI must break the loop.
Which group settings must be configured on VPC interface policy groups ipg_vpc-legacy_1 and
ipg_vpc-legacy_2 to meet these requirements?
- A. MCP: enabled BPDU Guard: enabled BPDU Filter: disabled
- B. MCP: enabled BPDU Guard: disabled BPDU Filter: disabled
- C. MCP: disabled BPDU Guard: disabled BPDU Filter: enabled
- D. MCP: disabled BPDU Guard: enabled BPDU Filter enable
Answer:
B
Question 15
Cisco ACI fabric contains a tenant called Prod. User_1 must have write access to tenant Prod and full
access to the fabric access policy. Which set of actions must be taken to meet these requirements?
- A. Associate User_1 to the fabric access policy. Associate the security domain to the fabric access policy. Create RBAC for the distinguished name of tenant Prod.
- B. Associate User_1 to tenant Prod. Associate the security domain to the distinguished name of the fabric access policy. Create RBAC for the distinguished name of security domain.
- C. Associate User_1 to the distinguished name of the fabric access policy. Associate the security domain to RBAC. Create RBAC for the distinguished name of User__1.
- D. Associate User_1 to the security domain. Associate the security domain to tenant Prod. Create RBAC for the distinguished name of fabric access policy.
Answer:
D