cisco 300-215 Exam Questions
Questions for the 300-215 were updated on : Feb 18 ,2026
Page 1 out of 8. Viewing questions 1-15 out of 116
Question 1
Refer to the exhibit.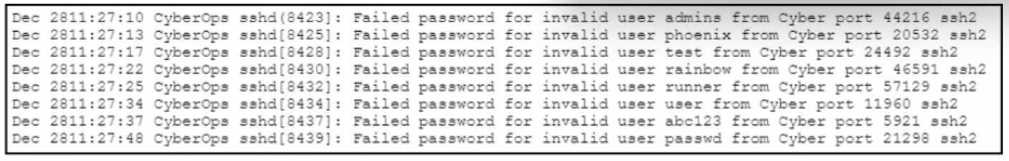
A web hosting company analyst is analyzing the latest traffic because there was a 20% spike in server
CPU usage recently. After correlating the logs, the problem seems to be related to the bad actor
activities. Which attack vector is used and what mitigation can the analyst suggest?
- A. SQL Injection; implement input validation and use parameterized queries.
- B. Distributed denial of service; use rate limiting and DDoS protection services.
- C. Phishing attack; conduct regular user training and use email filtering solutions.
- D. Brute-force attack; implement account lockout policies and roll out MFA.
Answer:
D
Explanation:
Comprehensive and Detailed
The log entries show repeated SSH login attempts for various invalid usernames (e.g., admin,
phoenix, rainbow, test, user, etc.) from different source ports. These are clear signs of a brute-force
attack—an automated process trying multiple usernames and passwords in hopes of gaining access.
Mitigating such attacks includes:
Implementing account lockout policies (e.g., locking an account after several failed login attempts).
Enabling Multi-Factor Authentication (MFA) to ensure that password guessing alone is insufficient for
account access.
Therefore, the correct answer is:
D . Brute-force attack; implement account lockout policies and roll out MFA.
Question 2
Refer to the exhibit.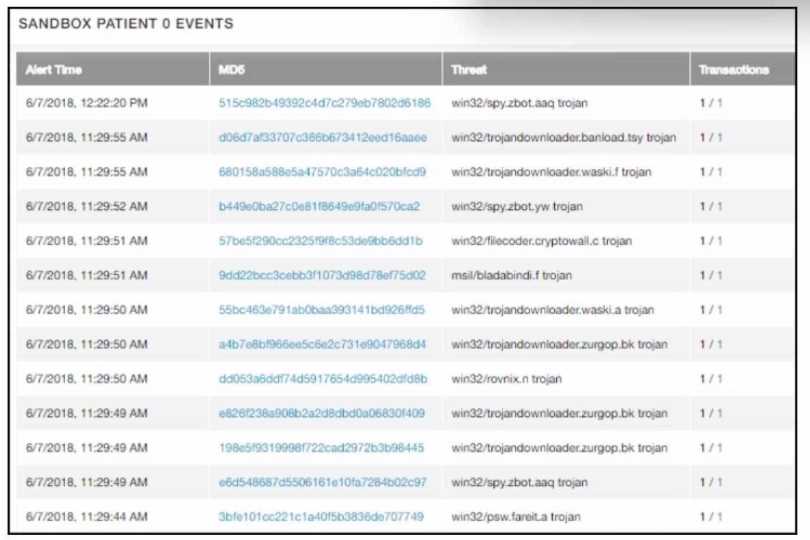
multiple machines behave abnormally. A sandbox analysis reveals malware. What must the
administrator determine next?
- A. if Patient 0 still demonstrates suspicious behavior
- B. source code of the malicious attachment
- C. if the file in Patient 0 is encrypted
- D. if Patient 0 tried to connect to another workstation
Answer:
D
Explanation:
The key goal during lateral movement analysis is to determine whether the malware spread or
attempted to spread beyond the initially compromised system. This is crucial for containment and
scoping of the incident. Logs, sandbox behavior, or network activity may show if Patient 0 initiated
outbound connections to other systems, potentially propagating malware across the environment.
Correct answer: D. if Patient 0 tried to connect to another workstation.
Question 3
Refer to the exhibit.
- A. hex encoding
- B. metamorphic encoding
- C. ASCII85 encoding
- D. Base64 encoding
Answer:
D
Explanation:
The string shown is long, alphanumeric, and includes both uppercase and lowercase letters with
numbers—characteristics of Base64 encoding. This format is widely used to obfuscate payloads in
malicious scripts, particularly in phishing or malware campaigns. Base64 encoding is also supported
by Python and other platforms for data transformation.
—
Question 4
Refer to the exhibit.
- A. VBScript
- B. Python
- C. Bash
- D. shell
Answer:
B
Explanation:
The code includes syntax and modules such as import win32con, import win32api, and uses Python-
specific formatting like def, try/except, and print, clearly indicating that this is written in Python. It
also uses the wmi module to monitor process creation events—a common technique in Python-
based process monitoring scripts on Windows.
—
Question 5
A cybersecurity analyst must identify an unknown service causing high CPU on a Windows server.
What tool should be used?
- A. Volatility to analyze memory dumps for forensic investigation
- B. Process Explorer from the Sysinternals Suite to monitor and examine active processes
- C. TCPdump to capture and analyze network packets
- D. SIFT (SANS Investigative Forensic Toolkit) for comprehensive digital forensics
Answer:
B
Explanation:
Process Explorer is an advanced Windows-based utility that shows real-time data about running
processes, CPU usage, services, DLLs, and handles. It is specifically designed for this kind of
investigation and is part of the Sysinternals Suite.
Question 6
Which issue is related to gathering evidence from cloud vendors?
- A. Deleted data cannot be recovered in cloud services.
- B. There is limited access to physical media.
- C. Forensics tools do not apply on cloud services.
- D. The chain of custody does not apply on cloud services.
Answer:
B
Explanation:
In cloud environments, investigators typically do not have access to the physical storage devices
where the data resides. This restricts traditional forensic processes, such as imaging or direct disk
access, which are commonly used in on-premises investigations.
Question 7
A cybersecurity analyst detects fileless malware activity on secure endpoints. What should be done
next?
- A. Immediately quarantine the endpoints containing the suspicious files and consider the issue resolved
- B. Isolate the affected endpoints and conduct a detailed memory analysis to identify fileless malware execution.
- C. Delete the suspicious files and monitor the endpoints for any further signs of compromise.
- D. Share the findings with other government agencies for collaborative threat analysis and response.
Answer:
B
Explanation:
Fileless malware resides in memory and does not leave traditional file artifacts, making it difficult for
antivirus solutions to detect. The most effective next step is to isolate the endpoints to prevent
lateral movement and perform memory forensics to capture volatile data and identify any running
malicious processes.
Question 8
An incident response analyst is preparing to scan memory using a YARA rule. How is this task
completed?
- A. deobfuscation
- B. XML injection
- C. string matching
- D. data diddling
Answer:
C
Explanation:
YARA rules are pattern-matching rules used to identify malware based on specific strings, conditions,
and binary patterns. They are most effective in memory or file scans where analysts search for known
indicators or unique signatures via string matching.
Correct answer: C. string matching.
Question 9
A malware outbreak revealed that a firewall was misconfigured, allowing external access to the
SharePoint server. What should the security team do next?
- A. Scan for and fix vulnerabilities on the firewall and server
- B. Harden the SharePoint server
- C. Disable external IP communications on all firewalls
- D. Review and update all firewall rules and the network security policy
Answer:
D
Explanation:
The incident stems from a policy-level issue rather than a technical vulnerability. According to
incident response best practices, the priority should be to review and update firewall rules and
ensure that the network security policy aligns with the principle of least privilege and correct access
segmentation.
Question 10
Data has been exfiltrated and advertised for sale on the dark web. A web server shows:
Database unresponsiveness
PageFile.sys changes
Disk usage spikes with CPU spikes
High page faults
Which action should the IR team perform on the server?
- A. Review the database.log file in the program files directory for database errors
- B. Examine the system.cfg file in the Windows directory for improper system configurations
- C. Analyze the PageFile.sys file in the System Drive and the Virtual Memory configuration
- D. Check the Memory.dmp file in the Windows directory for memory leak indications
Answer:
C
Explanation:
The combination of CPU spikes, disk usage peaks, and fluctuating PageFile.sys indicates excessive
virtual memory paging, which may be a sign of malicious memory or file access behavior.
PageFile.sys is part of the virtual memory system, and analyzing it can reveal which processes or
payloads are consuming unusual amounts of memory, especially during exfiltration events.
Question 11
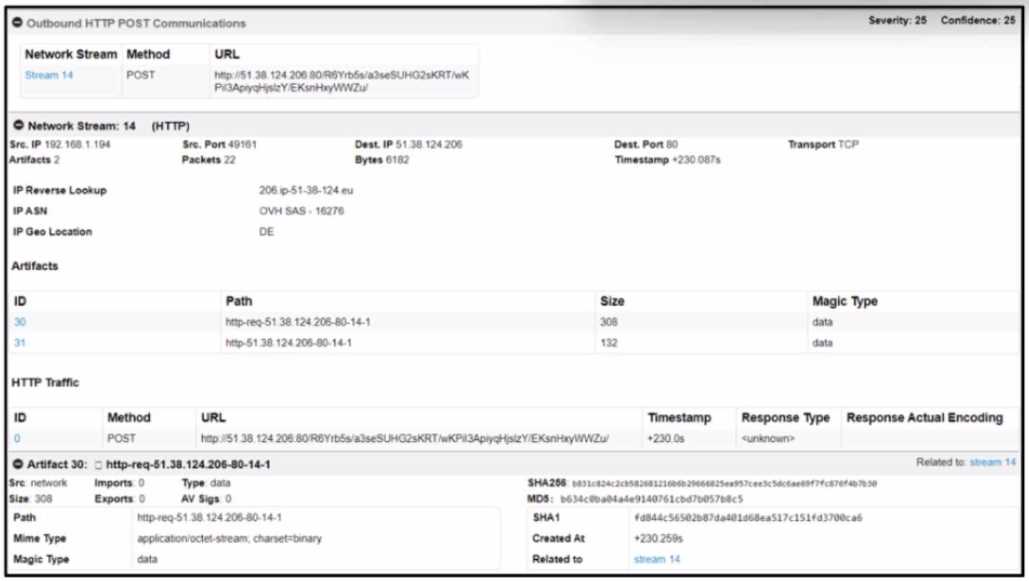
- A. Destination IP 51.38.124.206 is identified as malicious
- B. MD5 D634c0ba04a4e9140761cbd7b057t>8c5 is identified as malicious
- C. Path http-req-51.38.124.206-80-14-1 is benign
- D. The stream must be analyzed further via the pcap file
Answer:
A
Explanation:
Comprehensive and Detailed
From the exhibit, Cisco Secure Malware Analytics (formerly Threat Grid) has captured outbound
HTTP POST communication to the IP address 51.38.124.206 on port 80. This destination is
highlighted in the analysis under “Outbound HTTP POST Communications,” indicating exfiltration
behavior or command-and-control (C2) signaling.
Key indicators:
The report shows that binary data was POSTed to this IP.
The source system generated 22 packets and sent 6,192 bytes.
The system has flagged the behavior with a severity of 25 and confidence of 25—suggesting that this
is an IoC worth acting on.
Therefore, the artifacts suggest that the destination IP 51.38.124.206 is involved in malicious activity,
and the correct answer is:
Answer: A. Destination IP 51.38.124.206 is identified as malicious.
Explanation:
Question 12
A company had a recent data leak incident. A security engineer investigating the incident discovered
that a malicious link was accessed by multiple employees. Further investigation revealed targeted
phishing attack attempts on macOS systems, which led to backdoor installations and data
compromise. Which two security solutions should a security engineer recommend to mitigate similar
attacks in the future? (Choose two.)
- A. endpoint detection and response
- B. secure email gateway
- C. data loss prevention
- D. intrusion prevention system
- E. web application firewall
Answer:
A, B
Explanation:
Comprehensive and Detailed
Endpoint Detection and Response (EDR) tools provide behavioral analytics and continuous
monitoring to detect malware such as backdoors, which is especially critical on endpoints like macOS
devices. These tools are essential to detect post-compromise activities and contain threats before
they spread.
Secure Email Gateway (e.g., Cisco ESA) plays a key role in blocking phishing emails—the initial vector
in this attack. It uses filters and reputation analysis to prevent malicious links or attachments from
reaching end users.
Incorrect Options:
C. DLP focuses on preventing data exfiltration, not phishing prevention or backdoor detection.
D. IPS is effective for known signature-based threats but less effective against phishing links and
endpoint-level backdoors.
E. WAF protects web servers, not end-user devices from phishing or backdoor infections.
Therefore, the correct answers are: A and B.
Question 13
An analyst finds .xyz files of unknown origin that are large and undetected by antivirus. What action
should be taken next?
- A. Isolate the files and perform a deeper heuristic analysis to detect potential unknown malware or data exfiltration payloads.
- B. Rename the file extensions to .txt to enable easier opening and review by team members.
- C. Delete the files immediately to prevent potential risks.
- D. Move the files to a less secure network segment for analysis.
Answer:
A
Explanation:
The safest and most effective approach is to isolate the files and subject them to heuristic and
behavioral analysis. This can reveal obfuscated malware or unauthorized data storage techniques,
even if signature-based antivirus fails to flag them.
Question 14
A workstation uploads encrypted traffic to a known clean domain over TCP port 80. What type of
attack is occurring, according to the MITRE ATT&CK matrix?
- A. Exfiltration Over Web Service
- B. Exfiltration Over C2 Channel
- C. Exfiltration Over Asymmetric Encrypted Non-C2 Protocol
- D. Command and Control Activity
Answer:
C
Explanation:
According to the MITRE ATT&CK matrix, when encrypted traffic is tunneled through a legitimate
protocol such as HTTP (port 80) to a non-malicious domain, this aligns with the tactic “Exfiltration
Over Asymmetric Encrypted Non-C2 Protocol” (T1048.002). The attacker is trying to hide exfiltration
in otherwise benign traffic.
Question 15
What are two features of Cisco Secure Endpoint? (Choose two.)
- A. file trajectory
- B. rogue wireless detection
- C. Orbital Advanced Search
- D. web content filtering
- E. full disk encryption
Answer:
A, C
Explanation:
Cisco Secure Endpoint (formerly AMP for Endpoints) offers features like:
File trajectory: to track file behavior and spread across endpoints.
Orbital Advanced Search: for querying endpoint data to detect threats in real time.