cisco 200-201 Exam Questions
Questions for the 200-201 were updated on : Feb 26 ,2026
Page 1 out of 31. Viewing questions 1-15 out of 451
Question 1
Which type of attack involves sending input commands to a web server to access data?
- A. SQL injection
- B. Denial of service
- C. Cross-site scripting
- D. DNS poisoning
Answer:
A
Question 2
A data privacy officer at a marketing firm has received a request from a former client to delete all
personally sensitive information held by the company. The firm operates globally and follows
international data protection standards. The only information retained about the client is a unique
customer ID, "051473912", which is not directly tied to the name, address, or any other identifiable
details. Which action should the data privacy officer take?
- A. Delete the data immediately to comply with all global privacy regulations.
- B. Retain the data, as a customer ID by itself does not qualify as PSI under international standards.
- C. Consult the legal team, as customer IDs are always considered PSI and cannot be retained.
- D. Delete the data if the customer ID is stored alongside additional information that can identify the client.
Answer:
D
Question 3
DRAG DROP
Drag and drop the data sources from the left onto the corresponding data types on the right.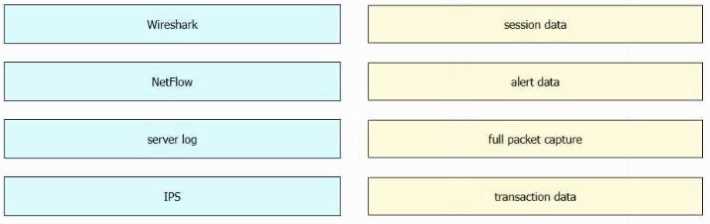
Answer:
None
Explanation: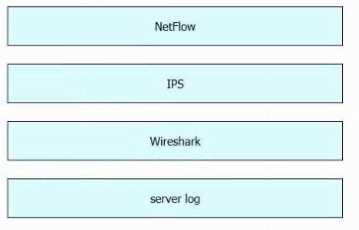
Question 4
Refer to the exhibit.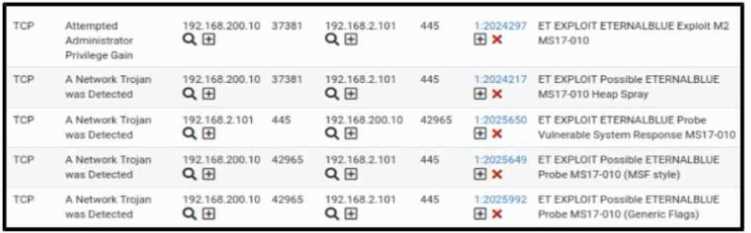
Refer to the exhibit. A security engineer receives several alerts from the SNORT IPS/IDS reporting
malicious traffic. What should the engineer understand by examining the SNORT logs?
- A. A remote threat performs an EternalBlue attack on a Windows system on several ports.
- B. An inside threat performs an EternalBlue attack on hosts 192.168.2.101 and 192.168.200.10 on port 445.
- C. A remote threat performs an EternalBlue attack on several hosts and different ports.
- D. An inside threat performs an EternalBlue attack on a Windows system on port 445.
Answer:
C
Question 5
Refer to the exhibit.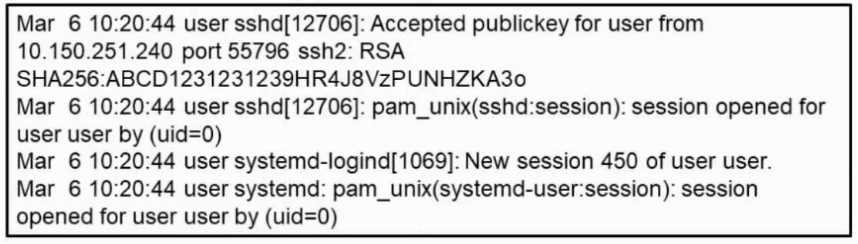
Refer to the exhibit. What occurred on this system based on this output?
- A. A user connected to the system using remote access VPN.
- B. A user created a new HTTP session using the SHA256 hashing algorithm.
- C. A user connected to the system after 450 attempts.
- D. A user connected to the system using SSH using source port 55796.
Answer:
D
Question 6
What is session data used for in network security?
- A. It is the transaction log between monitoring software.
- B. It contains the set of parameters used for fetching logs.
- C. It is the summary of the transmission between two network devices.
- D. It tracks cookies within each session initiated from a user.
Answer:
C
Question 7
An employee of a company receives an email with an attachment. They notice that this email is from
a suspicious source, and they decide not to open the attached file. After further investigation, a
security analyst concludes that this file is malware. To which category of the Cyber Kill Chain model
does this event belong?
- A. Weaponization
- B. Installation
- C. Exploitation
- D. Delivery
Answer:
D
Question 8
What does this regular expression do?
192|172).(168|1[6-9]|2[0-9]|3[0-1]).[0-9]{1,3}.[0-9]{1,3}\b
- A. It searches for private IP addresses except 10.0.0.0/8 IP address range.
- B. It matches any IP addresses within 172.16.0.0/16 IP address range.
- C. It searches for lines with private IP addresses in text.
- D. It extracts lines with 192.168.0.0/16 IP address range from the text.
Answer:
A
Question 9
Which scenario describes a social engineering attack?
- A. Malicious insider trying to gather information on company security
- B. Text message pretending to be from a legitimate company with a malicious URL inside
- C. Suspicious file detected on a workstation
- D. Company with a recent data breach where confidential information was stolen
Answer:
B
Question 10
A software development company develops high-end technology for the customer that will go
through the HIPAA audit program. The technology will be hosted in the cloud, and the healthcare,
employee names, and contact information will be stored on two separate logically isolated private
cloud services. The patents and inventions will be hosted on a separate encrypted database. A
compliance team is asked to analyze the cloud infrastructure and architecture to identify the
protected data. Which two types of protected data should be identified? (Choose two.)
- A. Federated Identity ID (FII)
- B. Protected Health Information (PHI)
- C. Personally Identifiable Information (PII)
- D. Payment Card Industry (PCI)
- E. Self-sovereign Identity (SSI)
Answer:
B, C
Question 11
A company recently encountered a breach. Critical services went through a disturbance and the
integrity of the data was altered. An engineer is investigating the issue and searching through the
logs in the SIEM. Which phase of the incident response is an engineer working on?
- A. post-incident and lessons learned
- B. recovery and restoration
- C. detection and analysis
- D. containment and eradication
Answer:
C
Question 12
Which CVSS metric group identifies other components that are affected by a successful security
attack?
- A. scope
- B. attack vector
- C. integrity
- D. privileges required
Answer:
A
Question 13
What is a difference between a threat and a vulnerability?
- A. A vulnerability is a risk of unauthorized actions from a threat actor, and a threat is the actions that malicious actors perform for privilege escalation.
- B. A threat is what an engineer is trying to protect an asset against, and a vulnerability is a weakness in an asset that an engineer is trying to mitigate.
- C. A vulnerability is an asset without hardened protection, and a threat is a weakness that is open to attackers due to misconfiguration.
- D. A threat is a weakness in an asset that an engineer is trying to mitigate, and a vulnerability is an existing risk of possible damage or loss of data.
Answer:
B
Question 14
Which statement describes threat hunting?
- A. It is an activity by an entity to deliberately bring down critical internal servers.
- B. It is a prevention activity to detect signs of intrusion, compromise, data theft, abnormalities, or malicious activity.
- C. It includes any activity that might go after competitors and adversaries to infiltrate their systems.
- D. It is a vulnerability assessment conducted by cyber professionals.
Answer:
B
Question 15
Which tool is used by threat actors on a webpage to take advantage of the software vulnerabilities of
a system to spread malware?
- A. script kiddie kit
- B. exploit kit
- C. vulnerability kit
- D. root kit
Answer:
B