cisco 100-160 Exam Questions
Questions for the 100-160 were updated on : Jan 20 ,2026
Page 1 out of 4. Viewing questions 1-15 out of 50
Question 1
During an incident response, the security team needs to isolate a compromised server from the rest
of the network but still allow forensic analysis. Which action should they take?
- A. Power off the server immediately.
- B. Disconnect the server from the network and connect it to an isolated forensic network.
- C. Delete suspicious files from the server.
- D. Reset all user passwords on the server.
Answer:
B
Explanation:
The CCST Cybersecurity course notes that isolation is a key part of the containment phase of incident
response. The goal is to prevent the compromised system from communicating with the attacker or
spreading malware, while preserving it for analysis.
"Containment often involves removing an affected system from the production network and
connecting it to a controlled forensic environment to preserve evidence and prevent further
compromise."
(CCST Cybersecurity, Incident Handling, Containment Procedures section, Cisco Networking
Academy)
Question 2
Which wireless security protocol provides the strongest protection for a home or small business
network?
- A. WEP
- B. WPA
- C. WPA2 with AES
- D. WPA3
Answer:
D
Explanation:
The CCST Cybersecurity Study Guide explains that WPA3 is the most current and secure Wi-Fi
Protected Access protocol, offering stronger encryption and better protection against brute-force
attacks compared to earlier versions.
"WPA3 improves wireless security by using more robust encryption methods and protections against
offline password guessing, making it the recommended protocol for securing modern Wi-Fi
networks."
(CCST Cybersecurity, Basic Network Security Concepts, Wireless Security Protocols section, Cisco
Networking Academy)
Question 3
A SOC analyst notices repeated failed login attempts from a foreign IP address followed by a
successful login to a privileged account. What is the most appropriate next step?
- A. Reset the affected user’s password and investigate the scope of compromise.
- B. Block all foreign IP addresses from accessing the network.
- C. Run a full vulnerability scan of the corporate network.
- D. Ignore the event unless it happens again.
Answer:
A
Explanation:
The CCST Cybersecurity course highlights that signs of brute-force attacks followed by successful
access require immediate account security actions and an investigation to determine if other systems
were accessed.
"When suspicious login activity is detected, immediate containment steps such as password resets
and log analysis are necessary to limit damage and identify the extent of the compromise."
(CCST Cybersecurity, Incident Handling, Account Compromise Response section, Cisco Networking
Academy)
Question 4
Which step should be performed immediately after identifying a critical vulnerability affecting
internet-facing systems?
- A. Document the vulnerability in the annual security report.
- B. Apply the vendor patch or mitigation.
- C. Schedule a quarterly penetration test.
- D. Change the default administrator passwords.
Answer:
B
Explanation:
The CCST Cybersecurity Study Guide states that after confirming a vulnerability is relevant and
critical, the next step is to apply available patches or mitigations as soon as possible to reduce the
attack surface.
"When a critical vulnerability is identified, remediation steps such as applying patches or
configuration changes should be implemented immediately to prevent exploitation."
(CCST Cybersecurity, Vulnerability Assessment and Risk Management, Vulnerability Remediation
section, Cisco Networking Academy)
Question 5
An administrator wants to ensure that any files downloaded from the internet are automatically
scanned for malicious code before execution. Which security control should be implemented?
- A. Host-based firewall
- B. Anti-malware with real-time protection
- C. VPN client
- D. Patch management system
Answer:
B
Explanation:
According to the CCST Cybersecurity course, anti-malware solutions with real-time protection scan
files as they are downloaded or opened, blocking malicious code before it runs.
"Real-time protection automatically inspects files, applications, and scripts as they are accessed or
downloaded, preventing execution of malicious code."
(CCST Cybersecurity, Endpoint Security Concepts, Malware Protection section, Cisco Networking
Academy)
Question 6
Which security measure can prevent unauthorized devices from automatically connecting to a
corporate network through unused switch ports?
- A. Port security
- B. VLAN trunking
- C. NAT
- D. VPN
Answer:
A
Explanation:
The CCST Cybersecurity Study Guide explains that port security on switches can be configured to limit
the number of MAC addresses allowed on a port, or to restrict it to specific devices.
"Port security can prevent unauthorized access by limiting or specifying the MAC addresses allowed
to connect through a given switch port. This mitigates risks from rogue devices connecting to the
network."
(CCST Cybersecurity, Basic Network Security Concepts, Switch Security section, Cisco Networking
Academy)
Question 7
You are reviewing the Application log on a Windows computer. You see an event with an error-level
message as shown.
What can you determine about the application that generated the event message?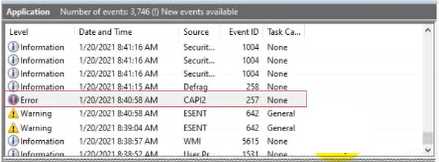
- A. The application is currently running much slower than expected.
- B. The application experienced a significant problem that caused it to fail.
- C. The application recovered from an event without loss of functionality.
- D. The application loaded and ran successfully without issues.
Answer:
B
Explanation:
In the CCST Cybersecurity course, Windows Event Viewer Error events in the Application log indicate
a severe problem that caused an application or component to fail. This usually requires investigation
or repair.
"Error events indicate a significant problem such as a loss of functionality in an application or system
component. Errors are often critical and need immediate attention."
(CCST Cybersecurity, Incident Handling, Event Logging and Analysis section, Cisco Networking
Academy)
A is incorrect: Performance slowness would usually generate warnings, not errors.
B is correct: An "Error" level in Event Viewer means the application failed in some way.
C is incorrect: That describes an "Information" event, not an error.
D is incorrect: That also corresponds to an "Information" event.
Question 8
You are collecting data after a suspected intrusion on the local LAN.
You need to capture incoming IP packets to a file for an investigator to analyze.
Which two tools should you use? (Choose 2.)
- A. Wireshark
- B. tcpdump
- C. Nmap
- D. netstat
Answer:
A, B
Explanation:
The CCST Cybersecurity Study Guide specifies that both Wireshark and tcpdump are packet capture
tools that can record network traffic to a file for later analysis.
"Wireshark provides a graphical interface for packet capture and analysis. Tcpdump is a command-
line tool that captures packets for detailed offline review."
(CCST Cybersecurity, Incident Handling, Network Traffic Analysis section, Cisco Networking Academy)
A is correct: Wireshark is widely used for packet capture and analysis.
B is correct: tcpdump is a CLI-based packet capture tool.
C (Nmap) is for network scanning, not packet capture.
D (netstat) displays network connections and ports but does not capture packets.
Question 9
DRAG DROP
Move each scenario from the list on the left to the correct type of attacker on the right.
Note: You will receive partial credit for each correct answer.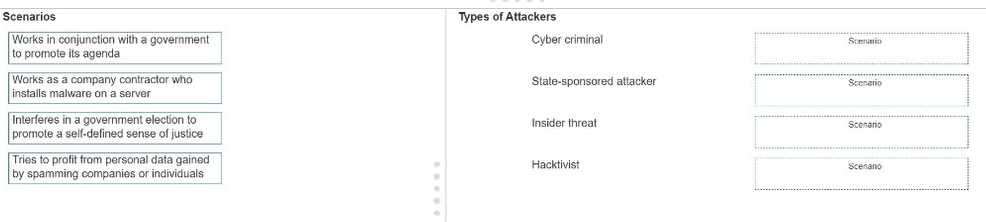
Answer:
None
Explanation: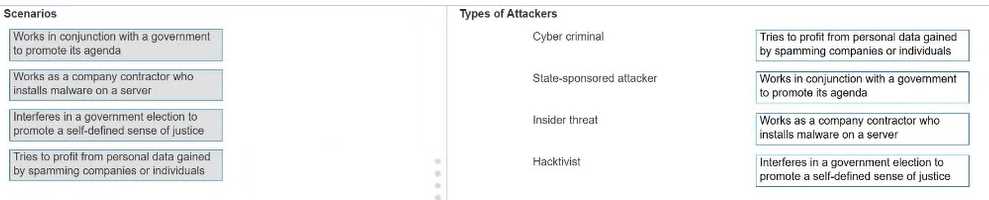
The CCST Cybersecurity Study Guide defines common attacker types:
Cyber criminal –
"An individual or group engaging in illegal activities for financial gain, such as selling stolen data or
running spam campaigns."
State-sponsored attacker –
"Operates with the support or direction of a nation-state, often for espionage or political objectives."
Insider threat –
"A person within the organization, such as an employee or contractor, who misuses access to cause
harm or steal data."
Hacktivist –
"Uses hacking techniques to promote political, social, or ideological causes."
(CCST Cybersecurity, Essential Security Principles, Threat Actor Types section, Cisco Networking
Academy)
Question 10
You need a software solution that performs the following tasks:
Compiles network data
Logs information from many sources
Provides orchestration in the form of case management
Automates incident response workflows
What product should you use?
- A. SIEM
- B. SOAR
- C. NextGen IPS
- D. Snort
Answer:
B
Explanation:
The CCST Cybersecurity Study Guide explains that SOAR (Security Orchestration, Automation, and
Response) platforms integrate data from multiple tools and sources, support case management, and
automate security workflows for faster incident response.
"SOAR solutions provide orchestration, automation, and response capabilities. They collect security
data from multiple systems, enable analysts to manage incidents, and automate repetitive tasks in
the response process."
(CCST Cybersecurity, Incident Handling, Security Automation Tools section, Cisco Networking
Academy)
A (SIEM) collects and correlates security logs but lacks full orchestration and automated response
capabilities.
B is correct: SOAR adds orchestration, case management, and automated incident response.
C (NextGen IPS) focuses on intrusion prevention, not orchestration.
D (Snort) is an open-source intrusion detection/prevention tool, not an orchestration platform.
Question 11
DRAG DROP
Move each framework from the list on the left to the correct purpose on the right.
Note: You will receive partial credit for each correct answer.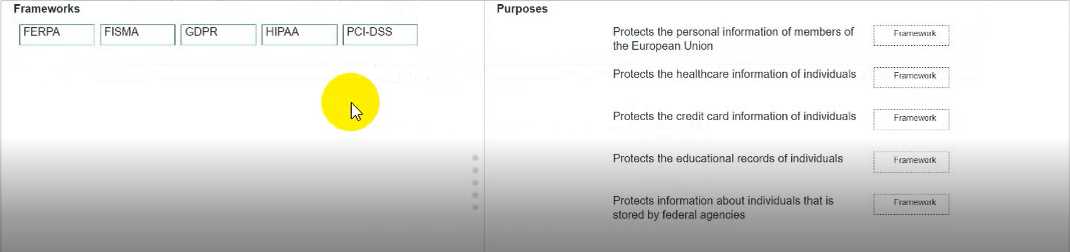
Answer:
None
Explanation: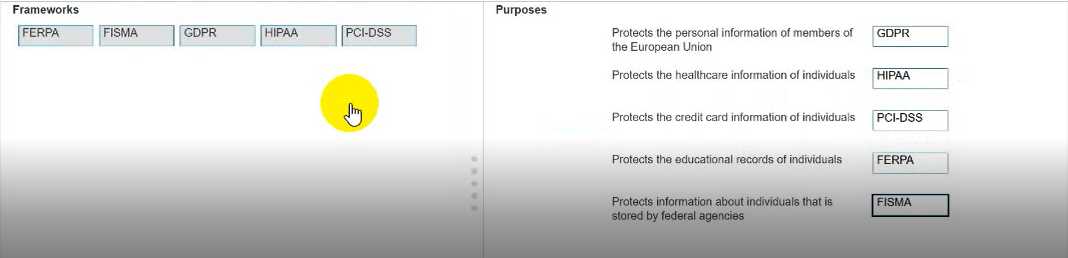
The CCST Cybersecurity Study Guide covers major privacy and security frameworks:
GDPR (General Data Protection Regulation) –
"EU regulation that protects personal data and privacy for individuals within the European Union."
HIPAA (Health Insurance Portability and Accountability Act) –
"US law that protects sensitive patient health information from being disclosed without the patient’s
consent or knowledge."
PCI-DSS (Payment Card Industry Data Security Standard) –
"Security standard to protect credit card data and reduce fraud."
FERPA (Family Educational Rights and Privacy Act) –
"US law that protects the privacy of student education records."
FISMA (Federal Information Security Management Act) –
"US law that requires federal agencies to protect information and information systems."
(CCST Cybersecurity, Essential Security Principles, Regulatory Compliance section, Cisco Networking
Academy)
Question 12
You need to design your company’s password policy to adhere to the National Institute of Standards
and Technology (NIST) guidelines for user password security.
What is the minimum password length that you should require to be consistent with the NIST
guidelines?
- A. 4 characters
- B. 8 characters
- C. 16 characters
- D. No minimum length
Answer:
B
Explanation:
According to the CCST Cybersecurity course, NIST guidelines (SP 800-63B) recommend a minimum
password length of 8 characters for user-generated passwords, without requiring overly complex
composition rules, but encouraging longer passphrases for increased security.
"NIST guidelines specify that user-generated passwords must be at least 8 characters in length, and
systems should allow passwords up to at least 64 characters."
(CCST Cybersecurity, Essential Security Principles, Authentication Best Practices section, Cisco
Networking Academy)
Question 13
You work for a hospital that stores electronic protected health information (ePHI) in an online portal.
Authorized employees can use their mobile devices to access patient ePHI.
You need to ensure that employees’ mobile devices comply with HIPAA regulations.
Which safeguard should you develop and implement?
- A. An ownership policy for employees’ mobile devices
- B. A contingency plan
- C. A policy that requires multi-factor authentication to use the mobile device
- D. A policy to govern how ePHI is removed from mobile devices
Answer:
D
Explanation:
The CCST Cybersecurity Study Guide notes that HIPAA (Health Insurance Portability and
Accountability Act) requires that ePHI be protected both in storage and when devices are
decommissioned or repurposed. This includes implementing data removal policies for mobile
devices.
"HIPAA requires procedures for the removal of electronic protected health information (ePHI) from
devices before disposal, reuse, or reassignment."
(CCST Cybersecurity, Essential Security Principles, Regulatory Compliance section, Cisco Networking
Academy)
Question 14
The company web server collects information through a form. The form is accessed by using port 80.
The form content is transferred to an encrypted database for storage. You are investigating a
complaint that the form content has been compromised.
What is the cause of the security breach?
- A. The database was compromised.
- B. The data was transferred to the database using a nonsecure protocol.
- C. The website was accessed using HTTP, which is an unencrypted protocol.
- D. The web browser used to access the site was not updated to the latest version.
Answer:
C
Explanation:
The CCST Cybersecurity Study Guide explains that HTTP (port 80) transmits data in cleartext, making
it susceptible to interception. Even if data is stored securely in an encrypted database, sensitive
information can be compromised during transmission if HTTPS (port 443) is not used.
"When HTTP is used instead of HTTPS, all form inputs and transmitted data are sent in plaintext over
the network, where they can be intercepted by attackers."
(CCST Cybersecurity, Basic Network Security Concepts, Secure Protocols section, Cisco Networking
Academy)
Question 15
Your supervisor tells you that you will participate in a CVSS assessment.
What will you be doing?
- A. Performing penetration tests on internal network devices and end systems
- B. Analyzing host logs to identify abnormal activities
- C. Interviewing users to determine their level of cybersecurity awareness
- D. Evaluating end system security and scoring software vulnerabilities
Answer:
D
Explanation:
The CCST Cybersecurity Study Guide explains that CVSS (Common Vulnerability Scoring System) is a
standardized method for rating the severity of software vulnerabilities. It considers exploitability,
impact, and environmental factors.
"The Common Vulnerability Scoring System (CVSS) provides a numerical score that reflects the
severity of a vulnerability, enabling prioritization of remediation efforts."
(CCST Cybersecurity, Vulnerability Assessment and Risk Management, Vulnerability Scoring section,
Cisco Networking Academy)