cisco 100-140 Exam Questions
Questions for the 100-140 were updated on : Jan 20 ,2026
Page 1 out of 3. Viewing questions 1-15 out of 42
Question 1
You are working from home over a weekend to resolve a backlog of employee help desk tickets. A
user issue requires you to access their Windows 11 computer in the home office to check its settings.
You have verified that the machine is available, but the user is not present.
Which remote access application is best suited for this task?
- A. Virtual Network Computing
- B. Remote Assistance
- C. Remote Desktop
- D. Remote Management
Answer:
C
Question 2
Which type of virtualization allows a user to run one or multiple operating systems that are stored
remotely on a central server in a data center?
- A. Data Virealization
- B. Storage Visualization
- C. Network Visualization
- D. Desktop Visualization
Answer:
D
Explanation:
Desktop virtualization (also known as Virtual Desktop Infrastructure, or VDI) enables users to run one
or more operating systems that reside on a centralized server in a data center, delivering the desktop
environment over the network.
Question 3
HOTSPOT
You consider using AI to find solutions to common Help Desk issues at your company.
For each statement about AI, select True or False.
Note: You will receive partial credit for each correct selection.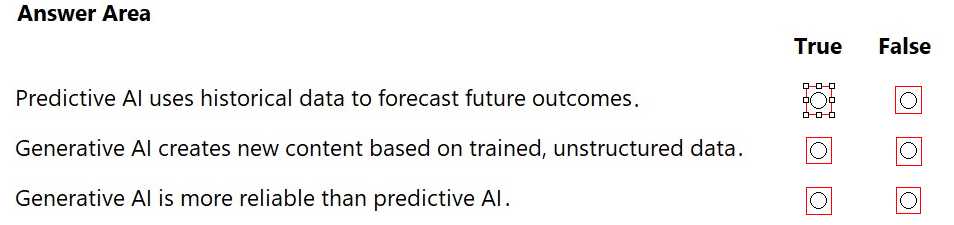
Answer:
None
Explanation: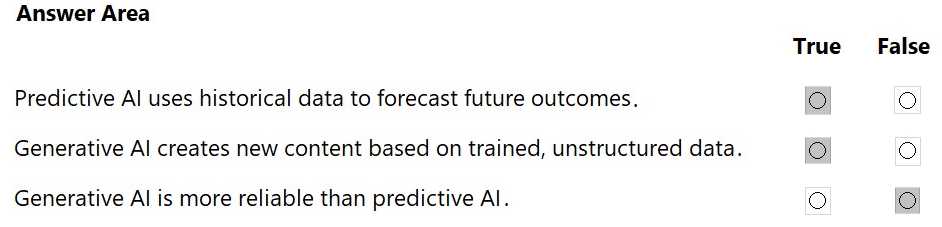
Question 4
DRAG DROP
Match each Windows tool from the list on the left to its appropriate usage scenario on the right.
Note: You will receive partial credit for each correct selection.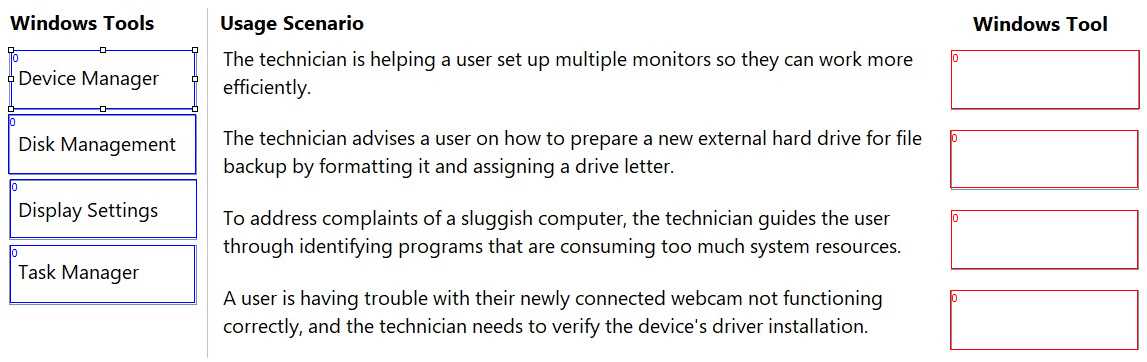
Answer:
None
Explanation: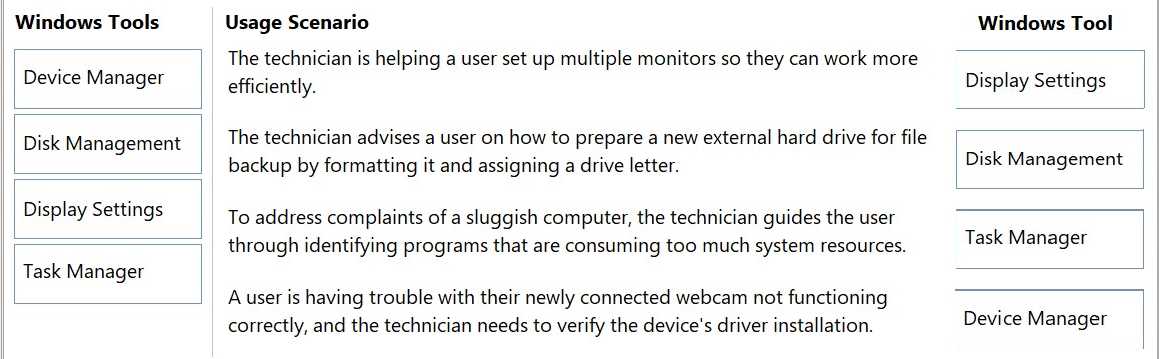
Question 5
A user needs to reset their password based on feedback after a security concern.
You want to provide an example of a strong password to the user based on the following company
guidelines shown:
Must have 8 to 15 characters
Must contain lowercase letters
Must contain at least 2 numbers
Must begin and end with a letter
Only special characters that can be used dash (-), underscore (_), hashtag (#), and at sign (@)
Which password could you use as an example?
- A. dkku546@
- B. j546h!Gg
- C. ywm546q
- D. mkn546#f
Answer:
D
Explanation:
mkn546#f is 8 characters long (within 8–15), begins with “m” and ends with “f” (letters), includes
only lowercase letters, contains three numbers (5, 4, 6), and uses only the allowed special character
“#.”
Question 6
A customer support representative receives an email from a client that contains their full name,
address, and credit card details and a request to update their billing information.
Which action should the representative take?
- A. Reply to the user and tell them to call the accounting department.
- B. Store the data on a personal device.
- C. Openly share the information with the accounting department.
- D. Store the data in encrypted storage.
Answer:
D
Explanation:
Payment card data and other sensitive personal information must be protected according to security
policies and compliance requirements (e.g., PCI DSS). Storing the data in approved encrypted storage
ensures it remains secure and accessible only by authorized personnel.
Question 7
Which three pieces of information would be considered Personally Identifiable Information (PII)?
(Choose three.)
Note: You will receive partial credit for each correct selection.
- A. Marital Status
- B. Fingerprint
- C. Email Address
- D. Gender
- E. Race
- F. Date of Birth
Answer:
B, C
Explanation:
Fingerprint is a unique biometric identifier and qualifies as PII.
Email Address directly identifies or contacts an individual.
Date of Birth is a personal datum that, when combined with other data, identifies someone.
Question 8
You receive an email from a user with the display name of the President of your company. The email
requests that you do them a favor and purchase gift cards and send the gift cards to an email address
provided.
What should you do?
- A. Call the number listed in the email.
- B. Reply to the sender asking them to verity the email's legitimacy.
- C. Call the IT department to verity that the email is valid.
- D. Purchase the gift cards and send them as the President asked.
Answer:
C
Explanation:
This scenario is a classic example of email spoofing and a social engineering attack. You should
contact the IT department immediately using internal communication methods to verify the
legitimacy of the request. Never respond or take action based on suspicious emails.
Question 9
You receive an email request for personal information.
You need to make sure you are working with the right individual to avoid a social engineering
attempt.
Which step should you take?
- A. Respond to the email request from the individual to ask them for personal information.
- B. Allow the individual to volunteer to share identity information.
- C. Use company approved methods to confirm the individual's identity.
- D. Share personal account information and ask the individual to confirm it.
Answer:
C
Explanation:
The safest and most professional approach is to use company-approved methods to verify identity,
such as callback procedures, employee ID verification, or multi-factor authentication. This helps
prevent falling victim to phishing or social engineering.
Question 10
What is the primary purpose of implementing a Mobile Device Management (MDM) solution in an
enterprise environment?
- A. To ensure that mobile devices comply with company policy before accessing the network.
- B. To track the user's location when at work or traveling for business.
- C. To authenticate users using an authenticator app on a mobile device.
- D. To allow the company to access the user's personal data.
Answer:
A
Explanation:
MDM solutions let IT enforce security policies — such as requiring device encryption, up-to-date OS
versions, PIN/passcode rules, and approved apps — before allowing mobile devices to connect to
corporate networks or access company data.
Question 11
A user who has been on vacation for the past 30 days calls the help desk and reaches you. The user
reports the following:
Before I left for vacation, I changed my password and made sure it worked. My password is not due
to be reset for another 60 days, but I can't log in to the network.
While the user was gone, the company established a requirement for Multi-Factor Authentication
(MFA).
Which two actions could you take to resolve the problem? (Choose two.)
Note: Each correct answer presents a complete solution.
- A. Tell the user to install the company's authenticator app.
- B. Set the user's password to never expire.
- C. Tell the user to add a phone number to their account for SMS validation.
- D. Unlock the user's account.
Answer:
A, C
Explanation:
Installing the company’s authenticator app enrolls the user in MFA as now required.
Adding a phone number enables SMS-based second-factor validation.
Question 12
HOTSPOT
Your company allows users to use their personal devices while in company meetings. However, the
computers must meet the following power management requirements:
The display must always turn black if the computer has no activity for 15 minutes.
The computer must always go into low-power mode if it has no activity for 30 minutes.
The computer must never hibernate.
You need to configure power management for a user's laptop to meet the requirements.
Select the correct options in the Power & Sleep settings window show in the answer area.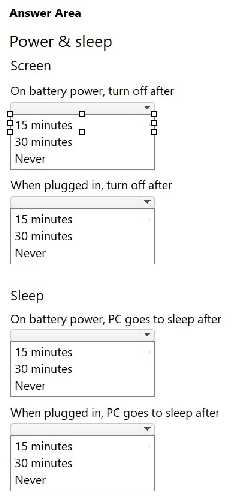
Answer:
None
Explanation: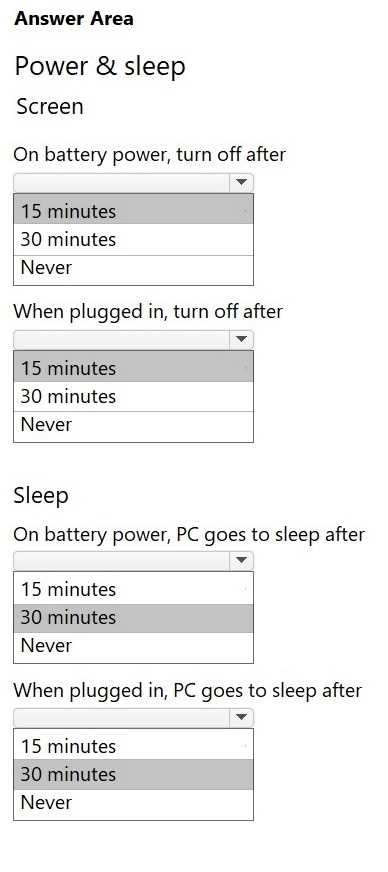
Question 13
HOTSPOT
A customer copied the APK file for an app from their Windows laptop to the Documents folder on
their Android phone. The customer needs help installing the app on the phone.
You need to configure the phone to allow installation of unknown apps.
Which option should you choose?
Select the correct option in the answer area.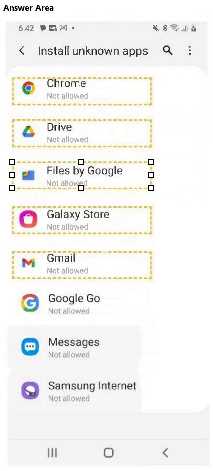
Answer:
None
Explanation: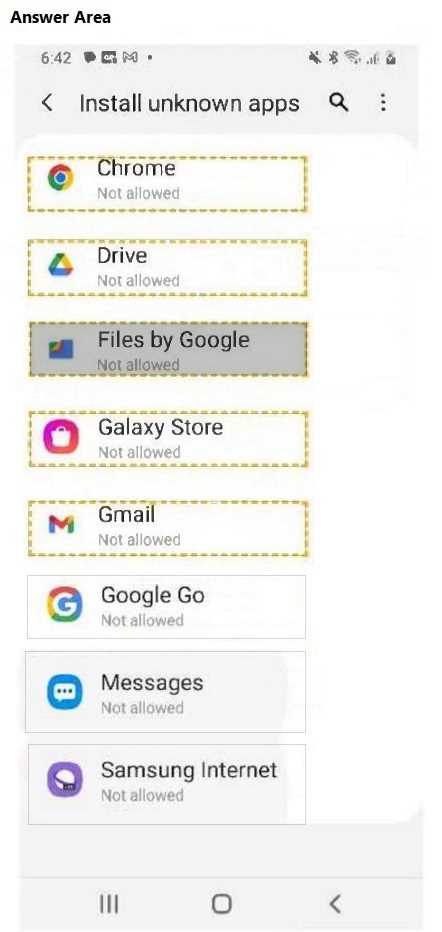
Question 14
A user needs assistance configuring Microsoft Teams so that it will start automatically.
Which category in Teams should the user select to set the application to auto-start?
- A. General
- B. Appearance and accessibility
- C. Notifications and activity
- D. Accounts and orgs
Answer:
A
Explanation:
The auto-start option for Teams is found under Settings > General, where you can toggle “Auto-start
application” to have Teams launch when you sign in.
Question 15
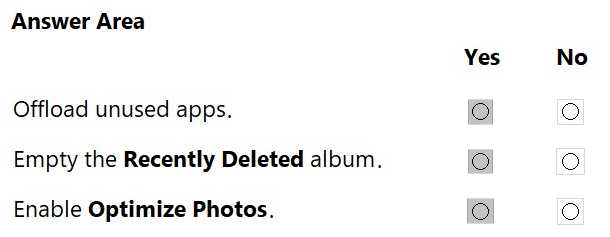
HOTSPOT
A user has low storage on an iPhone.
You need to tell the user how to increase available storage.
For each action, select Yes if it helps the user increase available storage, or No if it does not.
Note: You will receive partial credit for each correct selection.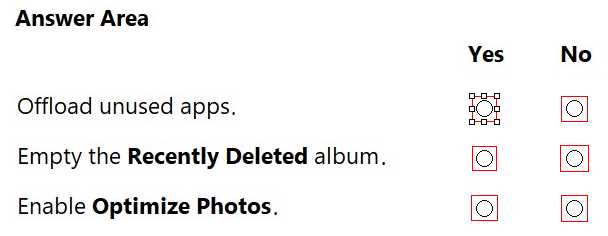
Answer:
None
Explanation: