CheckPoint 156-215-80 Exam Questions
Questions for the 156-215-80 were updated on : Jun 26 ,2025
Page 1 out of 35. Viewing questions 1-15 out of 522
Question 1
Which of the following is NOT an integral part of VPN communication within a network?
- A. VPN key
- B. VPN community
- C. VPN trust entities
- D. VPN domain
Answer:
A
Question 2
Two administrators Dave and Jon both manage R80 Management as administrators for ABC
Corp. Jon logged into the R80 Management and then shortly after Dave logged in to the same
server. They are both in the Security Policies view. From the screenshots below, why does
Dave not have the rule no.6 in his SmartConsole view even though Jon has it his in his
SmartConsole view?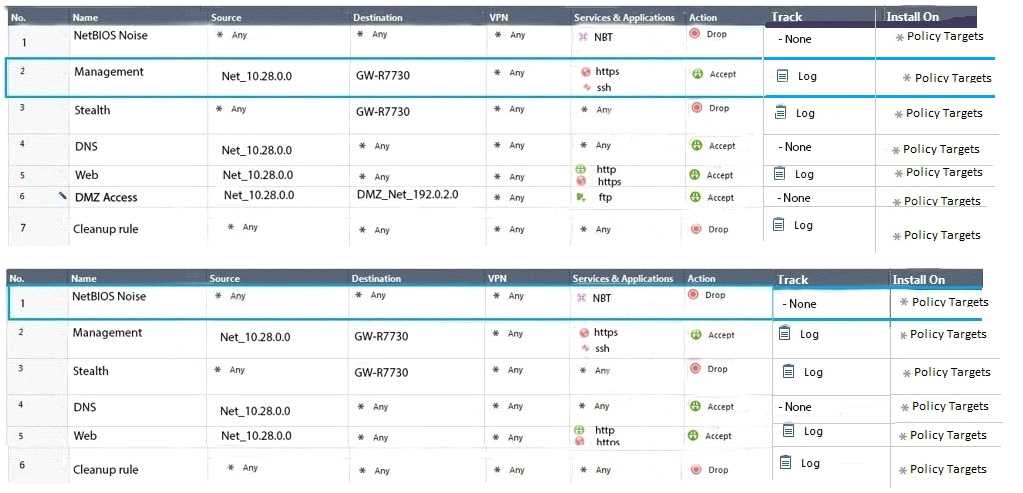
- A. Jon is currently editing rule no.6 but has Published part of his changes.
- B. Dave is currently editing rule no.6 and has marked this rule for deletion.
- C. Dave is currently editing rule no.6 and has deleted it from his Rule Base.
- D. Jon is currently editing rule no.6 but has not yet Published his changes.
Answer:
D
Explanation:
When an administrator logs in to the Security Management Server through SmartConsole, a
new editing session starts. The changes that the administrator makes during the session are
only available to that administrator. Other administrators see a lock icon on object and rules
that are being edited. To make changes available to all administrators, and to unlock the
objects and rules that are being edited, the administrator must publish the session.
Question 3
Vanessa is firewall administrator in her company; her company is using Check Point firewalls
on central and remote locations, which are managed centrally by R80 Security Management
Server. One central location has an installed R77.30 Gateway on Open server. Remote
location is using Check Point UTM-1 570 series appliance with R71. Which encryption is
used in Secure Internal Communication (SIC) between central management and firewall on
each location?
- A. On central firewall AES128 encryption is used for SIC, on Remote firewall 3DES encryption is used for SIC.
- B. On both firewalls, the same encryption is used for SIC. This is AES-GCM-256.
- C. The Firewall Administrator can choose which encryption suite will be used by SIC.
- D. On central firewall AES256 encryption is used for SIC, on Remote firewall AES128 encryption is used for SIC.
Answer:
A
Explanation:
Gateways above R71 use AES128 for SIC. If one of the gateways is R71 or below, the
gateways use 3DES.
Question 4
Review the following screenshot and select the BEST answer.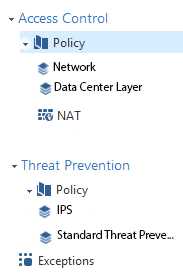
- A. Data Center Layer is an inline layer in the Access Control Policy.
- B. By default all layers are shared with all policies.
- C. If a connection is dropped in Network Layer, it will not be matched against the rules in Data Center Layer.
- D. If a connection is accepted in Network-layer, it will not be matched against the rules in Data Center Layer.
Answer:
C
Question 5
Which of the following is NOT a SecureXL traffic flow?
- A. Medium Path
- B. Accelerated Path
- C. Fast Path
- D. Slow Path
Answer:
C
Explanation:
SecureXL is an acceleration solution that maximizes performance of the Firewall and does
not compromise security. When SecureXL is enabled on a Security Gateway, some CPU
intensive operations are processed by virtualized software instead of the Firewall kernel. The
Firewall can inspect and process connections more efficiently and accelerate throughput and
connection rates. These are the SecureXL traffic flows:
Slow path - Packets and connections that are inspected by the Firewall and are not processed
by SecureXL.
Accelerated path - Packets and connections that are offloaded to SecureXL and are not
processed by the Firewall.
Medium path - Packets that require deeper inspection cannot use the accelerated path. It is
not necessary for the Firewall to inspect these packets, they can be offloaded and do not use
the slow path. For example, packets that are inspected by IPS cannot use the accelerated path
and can be offloaded to the IPS PSL (Passive Streaming Library). SecureXL processes these
packets more quickly than packets on the slow path.
Question 6
Which of the following Automatically Generated Rules NAT rules have the lowest
implementation priority?
- A. Machine Hide NAT
- B. Address Range Hide NAT
- C. Network Hide NAT
- D. Machine Static NAT
Answer:
B,C
Explanation:
SmartDashboard organizes the automatic NAT rules in this order:
Question 7
VPN gateways authenticate using ___________ and ___________ .
- A. Passwords; tokens
- B. Certificates; pre-shared secrets
- C. Certificates; passwords
- D. Tokens; pre-shared secrets
Answer:
B
Explanation:
VPN gateways authenticate using Digital Certificates and Pre-shared secrets.
Question 8
In R80 spoofing is defined as a method of:
- A. Disguising an illegal IP address behind an authorized IP address through Port Address Translation.
- B. Hiding your firewall from unauthorized users.
- C. Detecting people using false or wrong authentication logins
- D. Making packets appear as if they come from an authorized IP address.
Answer:
D
Explanation:
IP spoofing replaces the untrusted source IP address with a fake, trusted one, to hijack
connections to your network. Attackers use IP spoofing to send malware and bots to your
protected network, to execute DoS attacks, or to gain unauthorized access.
Question 9
The __________ is used to obtain identification and security information about network
users.
- A. User Directory
- B. User server
- C. UserCheck
- D. User index
Answer:
A
Question 10
Which Check Point feature enables application scanning and the detection?
- A. Application Dictionary
- B. AppWiki
- C. Application Library
- D. CPApp
Answer:
B
Explanation:
AppWiki Application Classification Library
AppWikienables application scanning and detection of more than 5,000 distinct applications
and over 300,000 Web 2.0 widgets including instant messaging, social networking, video
streaming, VoIP, games and more.
Question 11
DLP and Geo Policy are examples of what type of Policy?
- A. Standard Policies
- B. Shared Policies
- C. Inspection Policies
- D. Unified Policies
Answer:
B
Explanation:
The Shared policies are installed with the Access Control Policy.
Question 12
In which deployment is the security management server and Security Gateway installed on
the same appliance?
- A. Bridge Mode
- B. Remote
- C. Standalone
- D. Distributed
Answer:
C
Explanation:
Installing Standalone
Standalone Deployment - The Security Management Server and the Security Gateway are
installed on the same computer or appliance.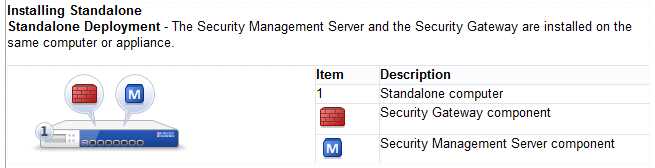
Question 13
A _________ VPN deployment is used to provide remote users with secure access to internal
corporate resources by authenticating the user through an internet browser.
- A. Clientless remote access
- B. Clientless direct access
- C. Client-based remote access
- D. Direct access
Answer:
A
Explanation:
Clientless- Users connect through a web browser and use HTTPS connections. Clientless
solutions usually supply access to web-based corporate resources.
Question 14
Which of the following statements is TRUE about R80 management plug-ins?
- A. The plug-in is a package installed on the Security Gateway.
- B. Installing a management plug-in requires a Snapshot, just like any upgrade process.
- C. A management plug-in interacts with a Security Management Server to provide new features and support for new products.
- D. Using a plug-in offers full central management only if special licensing is applied to specific features of the plug-in.
Answer:
C
Question 15
Gaia can be configured using the _______ or ______ .
- A. Gaia; command line interface
- B. WebUI; Gaia Interface
- C. Command line interface; WebUI
- D. Gaia Interface; GaiaUI
Answer:
C
Explanation:
Configuring Gaia for the First Time
In This Section:
Running the First Time Configuration Wizard in WebUI
Running the First Time Configuration Wizard in CLI
After you install Gaia for the first time, use the First Time Configuration Wizard to configure
the system and the Check Point products on it.