amazon AWS Certified Security - Specialty exam practice questions
Questions for the SCS-C02 were updated on : Feb 04 ,2026
Page 1 out of 30. Viewing questions 1-15 out of 450
Question 1
A company has AWS accounts in an organization in AWS Organizations. The company has enabled
Amazon GuardDuty in its production, support, and test accounts. The company runs important
workloads in the production account and centrally stores logs in an Amazon S3 bucket in the support
account.
A security engineer must implement a solution to elevate security findings for the production
account and the S3 bucket. The solution must automatically elevate findings of HIGH severity to
CRITICAL severity.
Which solution will meet these requirements?
- A. Enable AWS Security Hub for all accounts. In the Security Hub administrator account, enable the GuardDuty integration. Create automation rules to elevate findings for the production account and the S3 bucket.
- B. Enable AWS Security Hub for all accounts. In the Security Hub administrator account, enable the GuardDuty integration. Use Amazon EventBridge to create a custom rule to elevate findings for the production account and the S3 bucket.
- C. Use the GuardDuty administrator account to configure a threat list that includes the production account and the S3 bucket. Use Amazon EventBridge and Amazon Simple Notification Service (Amazon SNS) to elevate findings from the threat list.
- D. Use the GuardDuty administrator account to enable S3 protection for the support account that contains the S3 bucket. Configure GuardDuty to elevate findings for the production account and the S3 bucket.
Answer:
A
Question 2
A company is using AWS CloudTrail and Amazon CloudWatch to monitor resources in an AWS
account. The company's developers have been using an 1AM role in the account for the last 3
months.
A security engineer needs to refine the customer managed 1AM policy attached to the role to ensure
that the role provides least privilege access.
Which solution will meet this requirement with the LEAST effort?
- A. Implement AWS 1AM Access Analyzer policy generation on the role.
- B. Implement AWS 1AM Access Analyzer policy validation on the role.
- C. Search CloudWatch logs to determine the actions the role invoked and to evaluate the permissions.
- D. Use AWS Trusted Advisor to compare the policies assigned to the role against AWS best practices.
Answer:
A
Question 3
A security engineer is troubleshooting a connectivity issue between a web server that is writing log
files to the logging server in another VPC. The engineer has confirmed that a peering relationship
exists between the two VPCs. VPC flow logs show that requests sent from the web server are
accepted by the logging server, but the web server never receives a reply.
Which of the following actions could fix this issue?
- A. Add an inbound rule to the security group associated with the logging server that allows requests from the web server.
- B. Add an outbound rule to the security group associated with the web server that allows requests to the logging server.
- C. Add a route to the route table associated with the subnet that hosts the logging server that targets the peering connection.
- D. Add a route to the route table associated with the subnet that hosts the web server that targets the peering connection.
Answer:
C
Question 4
A security engineer needs to configure an Amazon S3 bucket policy to restrict access to an S3 bucket
that is named DOC-EXAMPLE-BUCKET. The policy must allow access to only DOC-EXAMPLE-BUCKET
from only the following endpoint vpce-1a2b3c4d. The policy must deny all access to DOC-EXAMPLE-
BUCKET if the specified endpomt is not used.
Which bucket policy statement meets these requirements?
A.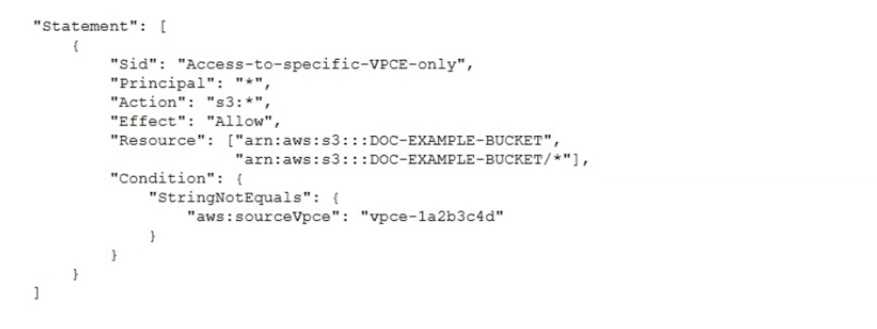
B.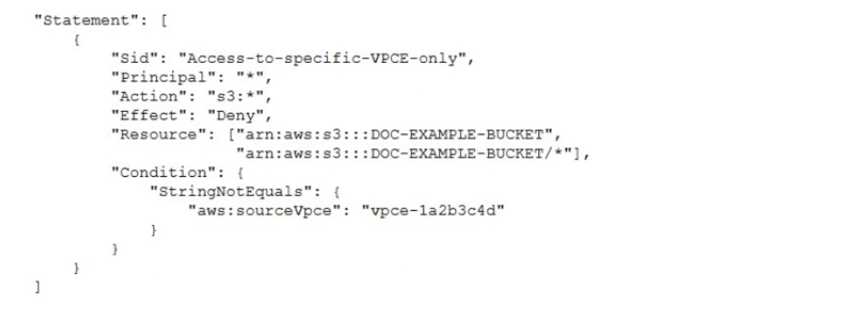
C.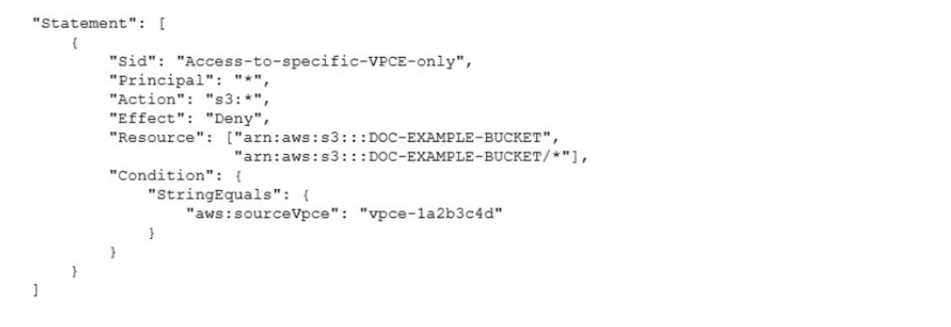
D.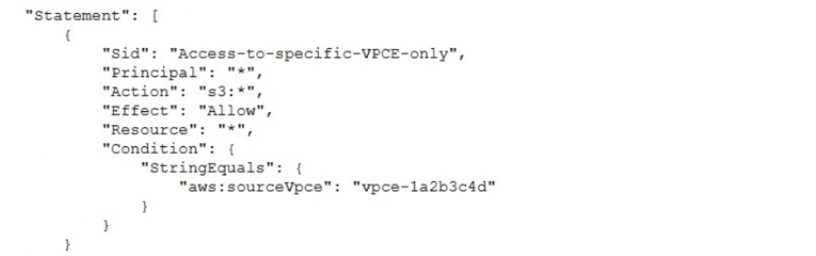
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
A
Question 5
A company that uses GitHub Actions needs to use a workflow to deploy AWS services. A security
engineer must set up authentication between the GitHub Actions workflow and the company's AWS
account.
The solution must involve no static credentials and no long-lived credentials for access to AWS
Additionally, the workflow must be able to run without requiring any manual changes.
Which solution will meet these requirements?
- A. Create an 1AM user Attach an 1AM policy to the 1AM user Use the AWS CLI to generate temporary credentials for the 1AM user Use the access key, secret key, and session token to authenticate to AWS from the workflow.
- B. Enable AWS 1AM Identity Center and configure it to use a local directory. Create a new service user in the 1AM Identity Center directory. Use the AWS CLI to generate temporary credentials for the service user Use the user ID and session token to authenticate to AWS from the workflow.
- C. Create an OpenID Connect (OIDC) identity provider (IdP) in 1AM Use GitHub as the provider. Create an 1AM role Attach the role to a trust policy that contains condition keys to restrict the GitHub repositones that will run the workflow. Use the role ARN to authenticate to AWS from the workflow.
- D. Configure Amazon Cognito and create an identity pool. Configure the identity pool for a SAML identity provider (IdP) Use GitHub as the provider. Create an 1AM role Attach the role to a trust policy that allows the sts AssumeRole action for Cognito Configure the workflow in GitHub to authenticate against the SAML IdP.
Answer:
C
Question 6
A company has several Amazon S3 buckets thai do not enforce encryption in transit A security
engineer must implement a solution that enforces encryption in transit for all the company's existing
and future S3 buckets.
Which solution will meet these requirements'?
- A. Enable AWS Config Create a proactive AWS. Config Custom Policy rule Create a Guard clause to evaluate the S3 bucket policies to check for a value of True for the aws SecureTransport condition key. If the AWS Config rule evaluates to NON_COMPLIANT, block resource creation.
- B. Enable AWS Config Configure the s3-bucket-ssl-requests-only AWS Config managed rule and set the rule trigger type to Hybrid Create an AWS Systems Manager. Automation runbook that applies a bucket policy to deny requests when the value of the aws SecureTransport condition key is False Configure automatic remediation Set the runbook as the target of the rule.
- C. Enable Amazon Inspector Create a custom AWS Lambda rule. Create a Lambda function that applies a bucket policy to deny requests when the value of the aws SecureTransport condition key is False Set the Lambda function as the target of the rule.
- D. Create an AWS CloudTrail trail Enable S3 data events on the trail. Create an AWS Lambda function that applies a bucket policy to deny requests when the value of the aws SecureTransport condition key is False. Configure the CloudTrail trail to invoke the Lambda function.
Answer:
B
Question 7
A company uses an organization in AWS Organizations to help separate its Amazon EC2 instances and
VPCs. The company has separate OUs for development workloads and production workloads.
A security engineer must ensure that only AWS accounts in the production OU can write VPC flow
logs to an Amazon S3 bucket. The security engineer is configuring the S3 bucket policy with a
Condition element to allow the s3 PutObject action for VPC flow logs.
How should the security engineer configure the Condition element to meet these requirements?
- A. Set the value of the aws SourceOrgID condition key to be the organization ID
- B. Set the value of the aws SourceOrgPaths condition key to be the Organizations entity path of the production OU
- C. Set the value of the aws ResourceOrgID condition key to be the organization ID
- D. Set the value of the aws ResourceOrgPaths condition key to be the Organizations entity path of the production OU
Answer:
B
Question 8
A company uses Amazon GuardDuty. The company's security engineer needs lo receive an email
notification for every GuardDuty finding that is a High severity level. Which solution will meet this
requirement?
- A. Create a verified identity for the email address in Amazon Simple Email Service (Amazon SES) Create an Amazon EventBridge rule that has the SES verified identity as the target Specify GuardDuty as the event source Configure the EventBridge event pattern to match High seventy findings.
- B. Create an Amazon Simple Notification Service (Amazon SNS) topic Subscribe the email address to the SNS topic. Create an Amazon EventBridge rule that has the SNS topic as the target Specify GuardDuty as the event source Configure the EventBridge event pattern to match High severity findings.
- C. Create an Amazon Simple Notification Service (Amazon SNS) topic Subscribe the email address to the SNS topic. Enable AWS Security Hub Integrate Security Hub with GuardDuty. Use Security Hub automation rules to publish High severity GuardDuty findings to the SNS topic.
- D. Enable AWS Security Hub Integrate Security Hub with GuardDuty. Use Secunty Hub automation rules to create a custom rule. Configure the custom rule to detect High seventy GuardDuty findings and to send a notification to the email address.
Answer:
B
Question 9
A company uses AWS Organizations to manage its AWS accounts. The company needs to enforce
server-side encryption with AWS KMS keys (SSE-KMS) on its Amazon S3 buckets Which solution will
meet this requirement?
- A. Edit the S3 bucket policies to require requests to include the s3 x-amz-server-side-encryption header.
- B. Edit the S3 bucket policies to require requests to include the s3 x-amz-server-side-encryption-aws- kms-key-id header.
- C. Create an SCP that requires requests to include the s3 x-amz-server-side-encryption header Attach the SCP to the root OU.
- D. Create an SCP that requires requests to include the s3 x-amz-server-side-encryption-customer- algorithm header Attach the SCP to the root OU.
Answer:
C
Question 10
A security engineer needs to detect malware on Amazon Elastic Block Store (Amazon EBS) volumes
that are attached to Amazon EC2 instances.
Which solution will meet this requirement?
- A. Enable Amazon GuardDuty Configure Matware Protection for EC2 Run an on-demand malware scan of the EC2 instances.
- B. Enable Amazon GuardDuty Configure Runtime Monitoring Enable the automated agent configuration for the EC2 instances.
- C. Enable Amazon Inspector Configure agentless scanning for the EC2 instances.
- D. Enable Amazon Inspector Configure deep inspection of the EC2 instances Run an on-demand scan of the EC2 instances.
Answer:
A
Question 11
A company is processing data on AWS. The data is transmitted by millions of connected devices and
is stored in Amazon RDS and Amazon DocumentDB (with MongoDB compatibility). The company
uses AWS Backup to back up the data.
The company needs a solution to preserve individual backup recovery points Ail related data and
metadata, such as character encodings and datatypes, must remain unchanged and protected from
deletion. Retention times for the data will vary from several days to several years.
Which solution will meet these requirements?
- A. Use AWS Backup to create legal holds for the recovery points.
- B. Export the backup data to Amazon S3 Create S3 Object Lock legal holds for the recovery points.
- C. Configure an AWS Backup Vault Lock in compliance mode.
- D. Configure an AWS Backup Vault Lock in governance mode.
Answer:
C
Question 12
A security engineer is configuring AWS. Config for an AWS account that uses a new 1AM entity When
the security engineer tries to configure AWS. Config rules and automatic remediation options, errors
occur in the AWS CloudTrail logs the security engineer sees the following error message "Insufficient
delivery policy to s3 bucket DOC-EXAMPLE-BUCKET, unable to write to bucket provided s3 key prefix
is 'null'."
Which combination of steps should the security engineer take to remediate this issue? (Select TWO.)
- A. Check the Amazon S3 bucket policy Verify that the policy allows the config amazon aws com service to write to the target bucket.
- B. Verify that the 1AM entity has the permissions necessary to perform the s3 GetBucketAc1 and s3 PutObjecj operations to write to the target bucket.
- C. Verify that the Amazon S3 bucket policy has the permissions necessary to perform the s3: GetBucketAcl and s3 PutObject" operations to write to the target bucket.
- D. Check the policy that is associated with the 1AM entity Verify that the policy allows the config amazonaws com service to write to the target bucket.
- E. Verify that the AWS Config service role has permissions to invoke the BatchGetResourceConfig action instead of the GetResourceConfigHistory action and s3 PutObject" operation.
Answer:
A, C
Question 13
A security engineer needs to suppress AWS. Security Hub findings automatically for resources that
have a specific tag attached.
Which solution will meet this requirement?
- A. Create a Security Hub automation rule Edit the rule to include the specific resource tag and the specific tag value as the criteria. Select the automated action to change the workflow status to SUPPRESSED.
- B. Select each Security Hub control that needs to be suppressed. Add an exception to each control to suppress any findings that contain the specific tag value if the resource contains the specific resource tag.
- C. Send each Security Hub finding to Amazon Detective Create an automated rule in Detective to suppress any findings that contain the specific resource tag and the specific tag value
- D. Send each Security Hub finding to Amazon Inspector. Configure a suppression rule to suppress any findings that contain the specific resource tag and the specific tag value.
Answer:
A
Question 14
A company has an external web application that runs on Amazon EC2 instances behind an
Application Load Balancer (ALB) within a VPC. The web application stores data in an Amazon RDS for
MySQL DB instance. The company uses a Linux bastion host to apply schema updates to the database
Administrators connect to the bastion host through SSH from their corporate workstations. The
following security groups are applied to the infrastructure.
• sgLB associated with the ALB
• sgWeb associated with the EC2 instances
• sgDB associated with the DB instance
• sgBastion associated with the bastion host
Which security group configuration will meet these requirements MOST securely?
A.
• sgLB Allow port 80 traffic and port 443 traffic from 0 0 0 0/0
• sgWeb Allow port 80 traffic and port 443 traffic from sgLB
• sgDB Allow port 3306 traffic from sgWeb and sgBastion
• sgBastion Allow port 22 traffic from the corporate IP address range
B.
• sgLB Allow port 80 traffic and port 443 traffic from 0 0 0 0/0
• sgWeb Allow port 80 traffic and port 443 traffic from sgLB
• sgDB Allow port 3306 traffic from sgWeb and sgLB
• sgBastion Allow port 22 traffic from the VPC IP address range
C.
• sgLB Allow port 80 traffic and port 443 traffic from 0 0 0 0/0
• sgWeb Allow port 80 traffic and port 443 traffic from sgLB
• sgDB Allow port 3306 traffic from sgWeb and sgBastion
• sgBastion Allow port 22 traffic from the VPC IP address range
D.
* sgLB: Allow port 80 traffic and port 443 traffic from 0.0.0.0/0
* sgWeb: Allow port 80 traffic and port 443 traffic from 0.0.0.0/0
* sgDB: Allow port 3306 traffic from sgWeb and sgBastion
* sgBastion: Allow port 22 traffic from the corporate IP address range
Answer:
A
Question 15
A company's security engineer has been asked to monitor and report all AWS account root user
activities.
Which of the following would enable the security engineer to monitor and report all root user
activities'? (Select TWO.)
- A. Configuring AWS Organizations to monitor root user API calls on the paying account
- B. Creating an Amazon EventBndge rule that will run when any API call from the root user is reported.
- C. Configuring Amazon Inspector to scan the AWS account for any root user activity
- D. Configunng AWS Trusted Advisor to send an email to the security team when the root user logs in to the console
- E. Using Amazon SNS to notify the target group
Answer:
B, E